The Adobe Acrobat Sign scam isn’t new... but it’s getting harder to catch.
We’re seeing a consistent influx of phishing emails that mimic real document workflows, blending fake links with legitimate branding, infrastructure, and sender domains.
That’s what makes these adobesign scams effective - they don’t look fake. A PDF share. A salary form. A “contract” sent through [email protected]. It all looks routine - especially in environments where users are used to signing things digitally and quickly.
This blog breaks down how the Adobe Acrobat scam works, why people keep clicking, and how your security team can build the reflexes that actually prevent compromise.
Adobe Acrobat scam emails are evolving - and they’re getting harder to spot
You can usually spot a phishing email a mile off - sloppy grammar, sketchy logos, some weird sense of urgency. But Adobe-themed attacks don’t play by those rules. It’s not clumsy. It’s polished. And that’s exactly why it works.
In practice, most Adobe impersonation emails look closer to the real thing than the average Microsoft or DocuSign phish. They’ve basically just copied a real Adobe notification and then just swapped out a few crucial details to redirect to a phishing link or fake login flow.
Worse, many of these phishing emails include legitimate links back to Adobe infrastructure. You might get a fake “PDF shared via Acrobat Sign” message... but when you check the URLs in the email body, they point to real adobe.com domains.
That tricks not just the user, but sometimes even spam filters and secure email gateways. We've seen actual Adobe emails flagged as spam because attackers are mimicking them so effectively.
Why is Adobe a prime target for attackers?
This isn’t random. Adobe Acrobat and Adobe Sign hit the sweet spot for scammers: broad usage, enterprise trust, and routine document workflows. Getting an email from Adobe (whether about a PDF, a contract, or a subscription plan) just doesn’t set off alarm bells the way more obvious scams might. That’s the social engineering playbook.
Users are used to trusting Adobe notifications. And unlike DocuSign or PandaDoc, which are often siloed to finance or HR, Adobe shows up everywhere - from marketing teams sending decks to IT provisioning software trials. It's unlikely all of the people getting the emails even use Adobe Sign but they’ll still click - just in case it’s legit.
The most common endgame is credential harvesting. But increasingly, attackers are chaining multiple steps - like embedding a passcode-protected PDF with a QR code that links to a fake Adobe login page. Sometimes, the phishing link isn’t in the email at all... it’s in the file. Or worse, the file just tells you to “open this in the latest version of Adobe Reader” and offers a link to… you guessed it, a fake download.
These tactics are effective because they blend in. They mimic what an actual email, an actual Adobe Sign flow, might look like. And that’s the point.
How are Adobe phishing emails bypassing filters?
Adobe campaigns borrow not just the look and feel of Adobe emails, but actual infrastructure: links to acrobat.adobe.com, file shares from real @adobe.com senders, even legitimate-looking PDFs that mimic internal workflows.
Trusted domains, misused links
This isn’t a case of lookalike domains or obvious spoofing. Attackers are increasingly using real Adobe services - sometimes chaining them through other trusted platforms like Microsoft. We’ve seen redirect paths that go from a SharePoint-hosted file → an Adobe-branded PDF → a fake login page. It’s not just phishing. It’s staged misdirection, designed to slip through filters and land in inboxes.
Weaponizing PDFs and QR codes
Many of these emails don’t contain phishing links at all - just a PDF. Sometimes passcode-protected. Sometimes carrying a QR code. The user opens the file (after entering a passcode shared in the email), scans the code, and lands on a credential harvester. It's a tactic built to evade link-based detection entirely.
Detection gets it wrong - on both ends
This overlap between fake and real isn’t just confusing for users... it’s confusing for filters too. We’ve seen legitimate Adobe Sign notifications flagged as spam because they look like phishing attempts. On the flip side, phishing emails that use Adobe infrastructure can sail past legacy email security tools and even some AI-powered platforms, especially if the malicious payload is delayed or offloaded into a document.
Real-world examples: What Adobe Acrobat Sign scams actually look like
Phishing emails don’t always scream “scam.” Below are real examples of Adobe Acrobat Sign scams submitted via the Hoxhunt network.
Salary adjustment with urgency cue
Subject: Your signature is required
Payload: A file titled SalaryIncreaseForm.pdf sent under the guise of a restructure form.
Deception layer: The attacker knows “salary” triggers curiosity and urgency. The phrase “all parties will receive a final PDF copy” mimics the language of legitimate Adobe Acrobat Sign flows, and the layout nails Adobe branding.
Why it works: Recipients assume this is related to a payroll update - especially in regions where salary reviews are quarterly.
Potential blind spot: Salary forms sound personal, not phishing-related - a classic case of social engineering leveraging HR-style e-signature workflows.

QR code phish
Subject: Payroll Agreement - Immediate Action Required
Payload: PDF with embedded QR code, linked to a fake Acrobat Reader login.
Deception Layer: No clickable links in the email body content - just a QR code in the PDF. This is a deliberate attempt to bypass email filters and URL-scanning engines.
Why it works: Users scan QR codes on instinct. And because the payload is embedded in a PDF (a format many still consider “safe”), even secure email gateways may allow it through.
Potential blind spot: No suspicious email address, no link in the initial email and the QR redirects from what appears to be a legitimate version of Acrobat.

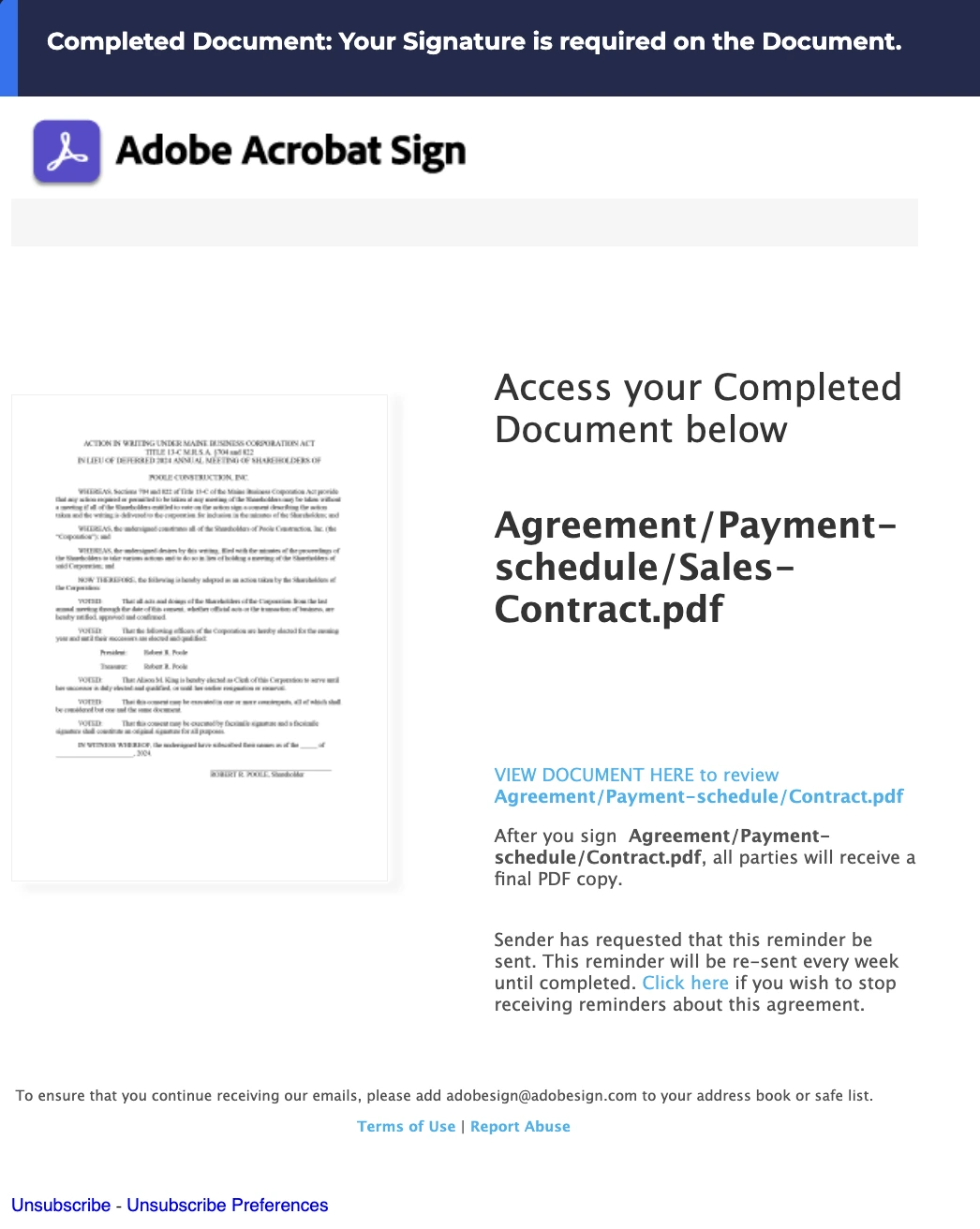
Invoice/contract loop with realistic reminder language
Subject: Completed Document – Your Signature Is Required
Payload: Contract link (Agreement/Payment-schedule/Contract.pdf) with auto-reminder
Deception layer: “This reminder will be re-sent every week until completed.” This language closely mimics actual Adobe Acrobat Sign reminder logic down to the unsubscribe link and reminder cadence.
Why it works: The attacker’s using real subscription logic (monthly subscription reminders, auto renewal cycles, etc.) to build familiarity and urgency.
Potential blind spot: Feels like a billing issue, not a threat, especially when paired with terms like “PDF copy,” “agreement,” and “sender has requested…”
RFP adjustment bait with generic branding
Subject: RFP Adjustments Pending Signature
Payload: “RFP-Adjustments.pdf” with CTA to Review & Sign
Deception layer: Very light branding, but structured like real Adobe communications. The filename reads like something from a procurement or sales ops flow which makes it relevant across departments.
Why it works: Targets mid-level roles who routinely deal with PDFs and approvals, without raising flags. “RFP” implies urgency, but not panic.
Potential blind spot: Leans on work language over flash - this isn’t spoofed to wow; it’s spoofed to blend in.

Board minutes + financial report lure
Subject: Board & Employee Minutes And Financial Report 2024
Payload: CTA button leading to “Open Meeting Schedules Online”
Deception layer: The attacker leans on formal corporate language - board meetings, attendance registration, financial reports. The email footer mimics Adobe legalese and compliance disclaimers almost verbatim, including privacy policy references and a fake unsubscribe link.
Why it works: High-trust, low-context - the email doesn’t scream urgency, it just sounds official. That tone makes people more likely to click without verifying.
Potential blind spot: Button CTA instead of raw URL, branding consistent with Adobe Document Cloud, and no obvious typos or red flags in the email body content. For AI-native email security solutions, it’s low signal and easy to confuse with a non-malicious email.

How to tell if an email claiming to be from Adobe is legitimate
Most Adobe-themed phishing emails don’t look broken. They look clean, on-brand, and convincing. But there are still markers if you know where to look.
1. The link doesn’t match the context
Even in highly convincing fakes, the core phishing link often doesn’t go to an actual Adobe domain, even if other links in the email do. All of the other links in the email might actually go to Adobe websites… except for the crucial one. Always hover over the “Review & Sign” or “Open Document” button and inspect the URL. If it’s not an adobe.com or adobesign.com domain, it’s likely fake.
2. The sender domain looks off or oddly generic
While some scams spoof @adobe.com convincingly, others rely on adjacent domains like @adobesign.co or generic email relay servers. If the email address doesn’t exactly match official Adobe senders, slow down. You can check raw email headers for inconsistencies - or better yet, compare it to an actual email from Adobe that you know is legitimate.
3. The email includes QR codes or password-protected PDFs
These aren’t signs of legitimacy - they’re evasive techniques. The PDF might even have passcode protection and then link to a credential harvester. Or worse, a QR code. If the email body content doesn’t mention a link - but the PDF does - treat it as high-risk.
4. The context doesn’t match how your org uses Adobe
If you don’t use Adobe Acrobat Sign for contracts, why would HR or finance be sending one? If the employees know how the process actually works, no matter how good the impersonation is, it doesn’t matter. Knowing your internal workflows is one of the most reliable protections you’ve got.
5. Overuse of urgency without specifics
Some fakes rely on vague cues like “Your signature is required today” or “Payroll adjustment attached” - without context or sender detail. That’s a red flag. Legitimate Adobe Sign requests typically include clear metadata: sender name, file purpose, agreement ID.
Got an email from Adobe Sign? Don’t assume it’s legit. Attackers are spoofing real workflows, real domains, and even real sender addresses.
Should we treat all unsolicited ‘Adobe Document’ share emails as suspicious by default?
Short answer? If you weren’t expecting it - pause.
That doesn’t mean every unsolicited Adobe Acrobat Sign notification is a scam. But the bar for trusting those emails should be much higher than it used to be. If you don’t use the Adobe platforms… then you might as well just ignore them. Even real emails can be risky if they trigger a click-first mindset.
There are a few reasons to be extra cautious:
- Legitimate Adobe emails get mimicked all the time. Attackers copy real Adobe share templates and only tweak the destination link. Even the unsubscribe and privacy footers get spoofed.
- Even real emails can be misused. We’ve seen cases where malicious actors use Adobe’s actual share tools to distribute phishing payloads, meaning a link from
@adobe.comisn’t automatically safe. - Scams often piggyback on expected workflows. The most convincing ones are designed to look like common HR or finance processes. Attacks around work contracts, handbooks, pay adjustments… we see a bunch of that at Hoxhunt. That overlap is what gets clicks.
The key isn’t to treat every Adobe share email as malicious... it’s to treat every unexpected one as potentially risky. Especially if it references a contract, invoice, payroll update, or board action you weren’t informed of elsewhere.
How can we train our employees to pause and verify Adobe links or sign-in requests?
Whether it’s a fake email from Adobe Sign or a spoofed Acrobat login, these threats are only getting more advanced. And the line between a real document and an Adobe Acrobat Sign scam isn’t always obvious. That’s why we train users to pause.
We don’t need everyone to become a forensic analyst. We just need them to be in the habit of pausing for two seconds before clicking.
That pause is the difference between a secure org and a compromised account.
But it doesn't come from generic training or compliance checklists. People don’t need walls of information... they need to know what to do in a certain situation. And traditional training - the kind that tells people to just “check the sender” or “look for typos - hasn’t kept up. It’s not tuned to realistic scams. It’s not built for Acrobat impersonation or QR-based phishing or OAuth abuse. And it’s definitely not designed for when attackers use real Adobe services to deliver fake documents.
That’s where our approach at Hoxhunt differs.
We build that pause reflex through continuous, context-aware phishing simulations. Users don’t just memorize rules. They build instincts. They see what a suspicious Adobe email actually looks like, they get it wrong (sometimes), and they learn what real-world threats feel like in their inbox. That’s what makes the behavior stick.
We also adapt difficulty over time. A beginner might get a low-stakes phishing email address test. But an employee further along in their training could be served a realistic spoof of an Adobe CC payroll update with a trusted link chain.
And when someone reports a suspicious email, we don’t just say “good job.” We give immediate feedback, tailored to what they saw and how they reacted.
Want to prevent Adobe Acrobat Sign scams?
Here’s what actually works:
- Simulate Adobe-specific phishing tactics (QR codes, legit sender domains, spoofed contract names)
- Build confidence through repetition, not just awareness slides
- Give people realistic, role-relevant scenarios, not generic phishing templates
- Empower users to report early and often, with positive reinforcement, not fear
Adobe Acrobat scams FAQ
Why do users keep falling for Adobe Acrobat sign scams?
Because they look legit and they feel expected. Adobe’s used across departments (HR, finance, ops), and users often assume PDF shares or Acrobat Sign requests are routine. Everyone has a salary. Everyone’s an employee. So something like a pay adjustment form feels normal. That familiarity bypasses suspicion.
What’s the most common Adobe-themed phishing scenario?
Credential harvesting - often through a fake PDF or QR-based redirect. One tactic involves an email with a PDF attachment, sometimes password-protected, that urges users to scan a QR code or open the doc in the “latest Adobe software.” The real payload lives behind that second step.
What’s the risk if someone clicks an Adobe phishing email link?
At minimum, they could be handing over credentials. In more advanced campaigns, attackers chain services, using Adobe-style links to redirect through Microsoft or OAuth flows. That opens up risks beyond the inbox: business email compromise, SharePoint access, or lateral movement across the entire organization.
Are similar impersonation scams happening with other platforms?
Yes, but Adobe impersonations are uniquely broad. With DocuSign or PandaDoc, it’s more department-specific. But Adobe gets used everywhere. We’ve even seen attackers use one Adobe service to spoof another - impersonating Acrobat via a legitimate Adobe Sign notification. That internal-brand crossover makes detection harder.
How should security teams train employees to spot Adobe Sign scams?
Start with realism, not theory. Generic phishing tips like “look for typos” or “check the sender” aren’t enough here. People may think a PDF is just a PDF - but that’s where the attack lives.
The key is to train people in context using actual Adobe-style phishing scenarios, not abstract rules. At Hoxhunt, we do this with targeted simulations that include real tactics attackers use: QR codes in PDFs, fake salary forms, spoofed sign-in requests. When users get exposed to those patterns in a safe environment, they build the reflex to pause and verify, even under pressure.
Training works best when it’s role-specific, behavior-driven, and delivered continuously - not once a year in a compliance video. That’s what we mean when we say: phishing awareness isn’t a knowledge problem. It’s a muscle-memory problem.
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt







