It's a malware jungle out there. Mounting cyber-attacks and successful data breaches, along with constantly evolving malware, have made us wary about, well, basically everything in our email. Clicking unknown links, downloading email attachments, enabling macros in office documents… the specter of malware lurks everywhere. And that specter moves and changes so quickly along a constantly-shifting threat landscape that people must now approach malware safety as a lifelong learning journey. Static guidelines won’t cut it.
Neither will the old line of malware safety thinking: “As long as I have my antivirus on, don’t download any attachments or enable macros on received documents, I’m safe, right?” Times have changed. As you’ll see below, just visiting a website can compromise your computer; and one wrong move could paralyze your whole company.
By mapping the different ways that malware can infect your device, you’ll be be better oriented to stay malware-free.
Points of entry: Social engineering | Drive-by download
Understanding the malware infection process means understanding how hackers get past the antivirus and human firewalls. They typically breach defenses either through social engineering or drive-by download.
In social engineering, the attacker presses emotional triggers to manipulate users into unwise actions, like downloading a malicious attachment from an email.
Drive-by downloading happens when malicious code is downloaded to the victim’s computer without their knowledge or consent.
How social engineering works
Some encounter social engineering on a daily basis in the form of phishing emails. These email scams are, after all, attackers' top malware delivery method. Attackers typically manufacture a sense of urgency, from subject line to email body, to induce an ill-considered action. “Urgent! Hurry! Quickly! immediately!” are common stress-inducing triggers for attention phishes.
Infecting a computer with malware requires manipulating the user into clicking or downloading one or more of the following from the phishing email:
- A link in the email body to a malicious or compromised site
- A malicious attachment
- PDF, HTM or HTML that redirects the user to a malicious website
- Office files containing macros
- Executable files
The below methods are the most common vectors of malware infection via phishing attacks.
Credential Harvesting
In credential harvesting attacks, attackers try to steal user credentials by spoofing landing pages into which someone would normally login. If one’s email account gets compromised:
- The attacker can send malicious emails to other contacts
- Email could be forwarded again and again
- More accounts could get compromised and perpetuate the cycle
- The bar for suspicion is set higher as the email is coming from a trusted sender
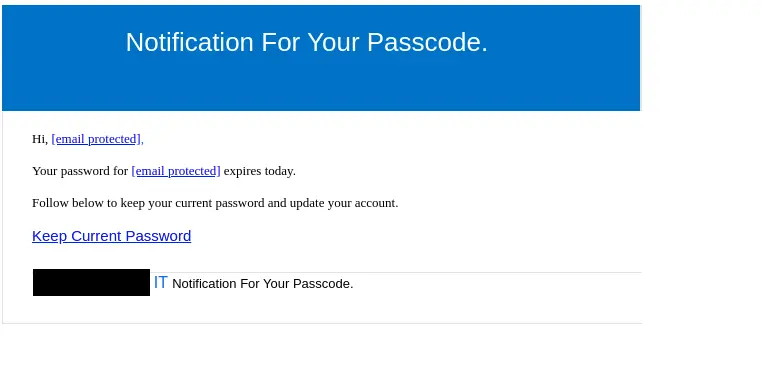
Example of a typical credential harvesting phish
Below you can see a typical phishing email. It claims that your email password is about to expire and you must change it immediately. If you click the link, you’ll likely be redirected to a clever-but-fake website created to steal your username and password to use for malicious purposes later on.
Downloading malicious attachments
Although email security protocols block some attachments automatically for security reasons, malicious emails still get through. Here are the most common types of malware in malicious email attachments:
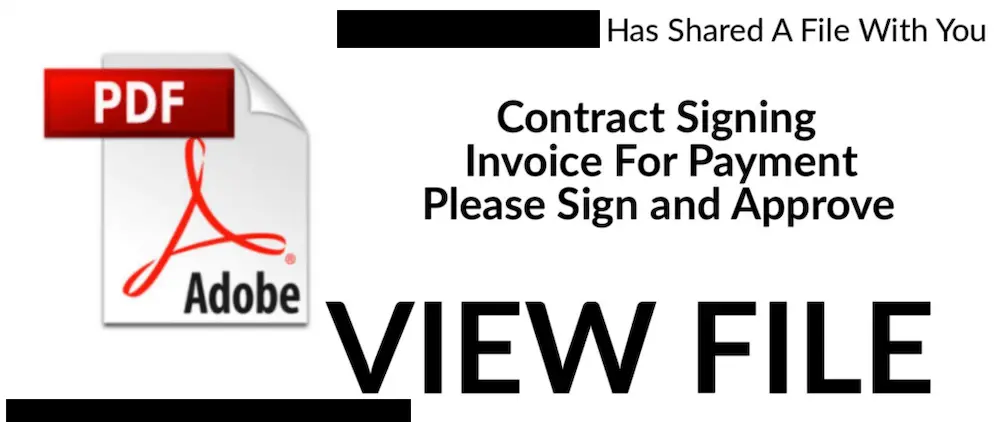
HTML, PDF or HTM documents
These kinds of documents don’t usually contain malware themselves. But rather, they contain a link that redirects the user to a malicious website, where the machine will be infected. Malicious attachments could also resemble a legitimate service containing login fields that, if filled in, would then compromise the user’s credentials and infect the machine.
How drive-by download malware works
Ransomware
Ransomware is one of the most dangerous forms of malware out there. Thrust into the spotlight with the infamous Colonial pipeline attack by the cyber gang DarkSide, ransomware has had a whole black market economy spring up around it that mimics traditional corporate kidnapping-for-ransom. It can have devastating financial and reputational consequences. This malicious software infects and encrypts computers with a password, locking out access and extorting ransom money, often in hard-to trace cryptocurrency, to unlock the files.
Check out our previous blogpost about ransomware to learn more.
Spyware
Spyware is malicious software that collects information about a user without their knowledge or consent. That information-- such as visited websites, credit card information, and so on-- is then sent to a hacker for malicious purposes.
Keylogger
Keylogger is a dangerous and invisible malware that records every keystroke of the user. This can result in compromised credentials, exposed credit card info, and much more.
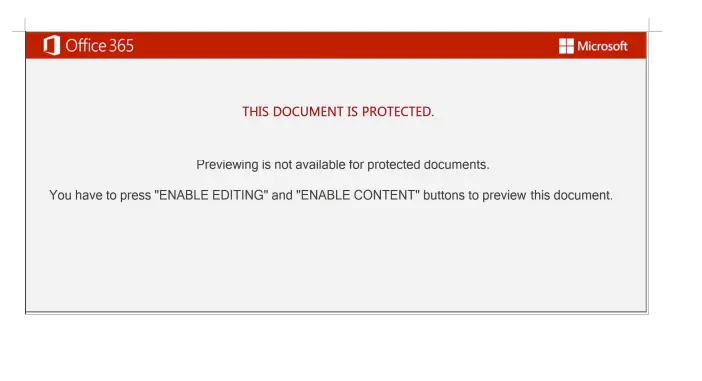
Macros
This is the type of malware often found in tainted office documents like Microsoft Excel or Word. If a user receives files that contain macros, they should be treated with caution.
Scripts found in malicious macros could potentially:
- Hijack your computer, gaining access to all of your files
- Download additional malware to your computer
- Delete your files
- Give hackers access to your files
And the worst part of it all is that the user won’t notice anything out of the ordinary, which makes this a textbook example of a drive-by download: “Downloading an application without user’s knowledge or consent.”
Example of a Microsoft word document with malicious macros
Stay protected with these 5 tips
- Never download email attachments from unknown sources
- If you are unsure about an email message received from a coworker, verify with them in a different channel
- Use extra caution when working with macro-enabled documents even if they’re from a trusted sender
- Were you expecting the email? If not, be extra careful!
- Never enable macros on documents unless absolutely required
Malicious web site infection
Just browsing a website is dangerous nowadays; using antivirus and not downloading anything won’t keep you entirely safe. Danger potentially lurks in malicious or compromised websites themselves in the form of ExploitKits.
ExploitKits, or EK’s, are hugely automated tools that are often placed in malicious or compromised websites that search for vulnerabilities in the user’s browser. They are currently one of the most-used methods of mass malware due to ease of use.
Upon visiting a compromised website, the EK automatically profiles if the user’s browser is patched and if any current exploits are available to use against that user’s browser. If the browser is fully patched to the latest version and no exploits are available, the exploit kit discontinues and the user is left alone. But when an exploit is discovered, a payload is sent to the host computer, which works as a file downloader for malware, which then infects the user’s machine.
This shows why keeping your browser updated is extremely important.
Stay protected against ExploitKits with these 3 tips:
- Visit only websites you trust
- Double check the URL for fake websites (i.e. hoxhunt.com vs hoaxhunt.com)
- ALWAYS keep your browser up to date to prevent hackers from using exploits against you
6 tips for navigating the malware jungle
It’s a digital jungle out there and malware is lurking everywhere, and in various forms. Online security should be taken as seriously as any other sort of safety precautions before traversing dangerous territory.
Fortunately, we can stay protected by following these 6 guidelines:
- Always keep your applications and browser up-to date with latest updates
- Don’t visit unknown or shady looking websites as this is risky
- Think twice before downloading any attachments from emails, especially if it’s from an unknown sender
- Keep an eye on the URL field to spot fake web addresses
- Don’t enter your credentials without thinking anywhere; take your time to inspect the environment
- Do not enable macros on documents unless absolutely necessary and if it’s from a trusted sender
Hoxhunt response
The Threat Analysis Team examines tens of thousands of reported phishing emails, including ones like these, a week–and have captured tens of millions of threats to date. They cluster the threats, rate them, and incorporate the nasty ones into our training simulations in real time to ensure our training stays at the cutting edge of the constantly-evolving threat landscape. Hoxhunt users are thus drilled on spotting and reporting the latest actual threats making the rounds, removing potentially catastrophic threats from your system with every push of the Hoxhunt reporting button.
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt







