Smishing (SMS-based phishing) has quietly become one of the hardest cyber attacks to stop. Text messages land on personal phones, bypassing email filters and security software, and in seconds employees can hand over passwords, account numbers, or credit card information.
To actually prevent smishing, you need behavior-change: realistic smishing simulations, smishing awareness training, and a culture that rewards fast reporting.
Smishing doesn’t look like a classic “cyber threat.” It looks like a delivery update, an order confirmation from an online retailer, or a bank website alert about suspicious activity. It hits people on the sofa at night, not just at their desk. That’s why traditional phishing tools, anti-malware software, and Office 365 mail filtering only cover part of the risk - most SMS phishing never touches your corporate infrastructure at all.
In this guide, we’ll break down how smishing works, why it’s so hard to block with technology alone, and how to prevent smishing.
What is smishing and why is it so hard to prevent?
Smishing is a type of phishing attack delivered via SMS text message, designed to trick users into revealing sensitive information or clicking malicious links. Unlike email phishing, smishing targets mobile devices directly - bypassing traditional security filters and reaching users in highly personal contexts. This makes smishing deceptively effective and notoriously difficult for organizations to defend against.
Why smishing evades traditional security measures
You can't block texts like you block emails.
Smishing doesn’t pass through corporate email gateways or filters. It hits users' personal phones - especially in Bring Your Own Device (BYOD) environments.
Here’s why that’s a problem:
- No native SMS filtering: Unlike email, SMS lacks widespread spam filtering or secure gateways.
- BYOD complications: Personal phones rarely have enterprise monitoring, making it hard to track incidents.
- Delayed detection: Attacks are often discovered only after credentials are stolen and abused.
- URL obfuscation: Attackers use short links or fake delivery messages that mimic legitimate brands (banks, couriers).

The human challenge
Even when trained, users still fall for smishing messages... especially during moments of distraction.
Research shows:
- Split-second decisions are common: Users act quickly on mobile notifications, especially when messages trigger fear, urgency, or curiosity.
- Repeat clickers exist in every organization: Despite training, some users consistently fall for well-crafted attacks.
- Cultural backlash is real: Overly punitive smishing simulations risk alienating employees rather than educating them.
The regulatory and privacy tightrope
Running smishing tests can trigger legal and ethical concerns:
- In the US and Canada: SMS simulations require explicit opt-in consent to comply with the Telephone Consumer Protection Act (TCPA).
- In Europe: Smishing simulations may be subject to works council approvals and GDPR scrutiny due to personal data usage.
Key smishing statistics to be aware of
- Only 23% of users over 55 can correctly define smishing, while 34% of millennials know the term.
- In one Lloyds TSB Study, only 18% of participants could correctly identify fake emails and texts.
- 17% of enterprise users encountered phishing links on their mobile devices.
- Smishing attacks surged 328% in 2020. In just one year, 76% of businesses were targeted by smishing attacks.
- Only 32% of organizations offer smishing simulations.
- Source: Keepnet
How smishing attacks work over text message (SMS)
Smishing attacks work by sending deceptive SMS text messages that impersonate banks, delivery services or internal IT, then pushing you to click a short URL or reply with sensitive data. On a mobile screen, these SMS phishing lures feel urgent and authentic, so users often act before checking the link or sender.
Attackers make initial contact via SMS
- Smishing attacks start with an SMS message.
- Attackers create messages that appear to come from trusted organizations.
- These messages are generally designed to exploit trust and often create a sense of urgency.
- Example message: “Your account is locked. Click this link to unlock it.”
Messages contain malicious links or requests
- SMS messages sent by attackers typically contain a malicious link or ask the recipient to reply with personal information.
- Clicking on the link usually leads to a fake website mimicking a legitimate service.
- Victims are prompted to enter sensitive data, such as login credentials, banking information, or two-factor authentication codes.
Social engineering tactics are used to trick targets
- Smishing relies heavily on social engineering techniques.
- Attackers use psychological manipulation to pressure victims into taking action quickly.
- The quicker someone acts, the less likely they are to scrutinize the suspicious message.
- Messages often use fear or urgency to bypass typical cautionary steps.
- Example: “If you don’t act in the next 24 hours, your account will be suspended.”
Gaining access or deploying malware
- Stealing credentials: Threat actors gain unauthorized access to corporate systems or personal accounts.
- Deploying malware: Malware can be installed on mobile devices, giving attackers control over the device and access to corporate emails or confidential data.
- Exposing victims to other risks: Targets may also fall victim to network infiltration, intellectual property theft, or compromise of sensitive data.

Smishing red flags employees should learn to spot
You can prevent most smishing attacks by teaching employees a short checklist of red flags: unexpected SMS, urgency or fear, requests for sensitive data or MFA codes, and shortened or strange URLs. When any two of these appear together in a text message, the safest move is to stop, verify via another channel, and report.
Core red flags to teach employees
- Out-of-the-blue security or money texts: Claims about blocked credit cards, bank account problems, tax refunds, payroll issues, or delivery failures when the user wasn’t expecting anything.
- Pressure + emotion: Language that creates fear or urgency (“account locked in 30 minutes”, “final notice”) is a classic social-engineering tactic to short-circuit judgment.
- Requests for sensitive information: Any SMS asking for passwords, banking information, credit card details, Social Security Number, or multi-factor authentication codes (e.g. from Google Authenticator) is almost certainly malicious.
- Suspicious or shortened URLs: Short links or domains that don’t clearly match a known bank, delivery service, or company site. On mobile, these are hard to inspect—train people to open trusted apps directly instead of tapping links.
- Odd senders or new threads: A “bank” or “IT” text coming from a new random number, unfamiliar short code, or a fresh thread instead of the usual conversation.
Simple rule for employees: If a text is unexpected, urgent, and asks you to click a link or share sensitive data, treat it as smishing: pause, verify using a trusted channel, then report.

Why traditional smishing prevention measures aren’t enough
Traditional controls miss smishing because SMS lives on personal phones, outside email filters and most corporate tooling. This leaves you with a gap that only behaviour-focused smishing training and easy reporting can realistically close.
Your tech stack doesn’t really see SMS
- Secure Email Gateways, spam filters, and email-focused security never touch SMS.
- Smishing lands in native messaging apps on mobile phones, often personal/ unmanaged devices.
- In practice, you can reliably measure only clicks and reports, not delivery or opens.
BYOD, mobile, and legal friction
- Many high-risk actions (bank alerts, MFA codes, payroll checks) happen on personal devices you don’t fully control.
- In US/Canada, mass SMS (including simulations) requires opt-in consent and a registered toll-free number; in EU, phone numbers are personal data under GDPR and often need extra approvals.
Typical training plateaus
- Annual videos and one-size-fits-all phishing tests drive compliance, not behavior change.
- Punishing repeat clickers (extra modules, HR escalations, even firing) kills psychological safety and makes people hide mistakes instead of reporting them.
What this means for smishing
To actually reduce risk from SMS phishing, you need to:
- Run realistic smishing simulations that respect legal/HR boundaries.
- Provide micro-training in the moment of failure or success, not once a year.
- Make SMS reporting effortless and reward users for it.
How smishing awareness training helps prevent attacks
Smishing awareness training helps prevent attacks by giving employees realistic practice spotting malicious SMS, rewarding reporting, and feeding real-time threat intel back to security teams. Done well, it’s continuous, personalized, and focused on behavior change.
What good smishing training actually changes
Effective programs move three needles at once:
- Recognition: Users see common smishing patterns (short URLs, fake bank/delivery texts, MFA scams) in realistic simulations, so real SMS phishing feels familiar.
- Reaction: Training hardwires a simple habit: pause → verify in a trusted app or website → report instead of clicking.
- Reporting: Every reported SMS (simulation or real) flows into a central threat feed, giving security teams visibility into attacks hitting mobile phones and letting them respond faster.
Why simulations + micro-training work better than slides
Here's what smishing training looks like in Hoxhunt:
- Realistic SMS simulations are sent to employees’ phones, mirroring genuine banking, delivery, or IT-themed scams but in a safe way.
- When a user reports a simulation, they get instant feedback and a short, focused micro-training explaining the trick used - plus a gamified reward (stars) to positively reinforce the behaviour.
- If they report a real smishing attempt, they’re thanked and shown an AI-powered analysis, turning a near-miss into a learning moment without blame.
This practice → feedback → reward loop is exactly what behavioral science says you need to build lasting habits and it avoids the punitive approaches that make people hide mistakes instead of reporting them.
From training to a human sensor network
At scale, smishing awareness training doesn’t just reduce individual risky clicks; it turns your workforce into a human sensor network:
- More employees reporting suspicious SMS messages from their mobile phones.
- Better visibility into which brands, lures, and phone numbers attackers are abusing.
- Faster, data-driven decisions on where to tighten controls.
AI-powered smishing awareness training: simulating real-world text message Attacks
Hoxhunt’s smishing training uses AI to send realistic SMS simulations to employees’ phones, coach them in the moment, and turn every reported text into threat intelligence. Instead of one-off tests, users get ongoing micro-exercises and rewards, while security teams gain visibility into real smishing hitting mobile devices.
How Hoxhunt smishing simulations work
- Send realistic SMS simulations that mimic bank, delivery, IT and HR scams, tailored to local regions (US, Canada, most EU countries).
- Use AI and behavioral science to individualize difficulty based on each employee’s past performance and role.
- Require phone numbers and (where needed) opt-in consent, so campaigns stay compliant while still testing real-world scenarios.
Reporting and coaching via the Hoxhunt iOS app
The Hoxhunt iOS app turns every suspicious text into a training and detection opportunity:
- Users report SMS through the native “Report Message” button in iOS; the message is sent straight to Hoxhunt with two taps.
- If it’s a simulation, they receive a push notification, earn stars, and can complete a short micro-training explaining the smishing tactics used.
- If it’s a real smish, they see an AI-powered analysis of why it’s risky and what to do next, while the case is forwarded to security.
Turning reports into smishing intelligence
On the backend, Hoxhunt treats SMS reports as a first-class signal:
- All reported SMS (real and simulated) flow into a central threat feed where machine learning classifies and prioritizes threats.
- With Hoxhunt Respond, smishing messages are clustered in incident orchestration and can be pushed into SIEM/SOAR stacks for faster response.
- Dashboards track smishing fail rate, reporting rate, and reporting speed, givingyou clear metrics on how mobile phishing risk is changing over time.
Together, this turns smishing training from a one-off SMS blast into a living system: employees practice on real-looking texts, get rewarded for reporting, and your team finally sees what’s happening on the SMS channel.
Smishing awareness training with gamification: keeping employees engaged
Gamified smishing training keeps people coming back: instead of punishing clicks, you reward fast reporting and improvement. Hoxhunt does this by turning every reported SMS into points, stars, and micro-wins, so employees treat smishing simulations like a quick game instead of another compliance chore.
Why gamification works for smishing
Gamification maps directly to what behavioral science says about habit change:
- Positive reinforcement beats punishment: rewarding correct actions changes behavior more reliably than reprimands or shaming.
- Small, frequent wins: short challenges plus instant feedback work better than annual “mega trainings” that nobody remembers.
- Safe practice with emotion: realistic, slightly “spicy” simulations trigger the same feelings as real scams, but in a safe, coached environment.
For smishing, where decisions are fast and emotional, that pattern is exactly what you need.
How Hoxhunt gamifies smishing training
Hoxhunt bakes gamification into its smishing flow, not as an afterthought.
- Stars for spotting simulations: When users report a Hoxhunt SMS simulation, they immediately earn stars for recognising the attack.
- Bonus stars via micro-training: A push notification takes them to a bite-sized micro-training explaining the specific smishing trick. Finishing it earns an extra star and reinforces the lesson in under a minute.
- Progress over perfection: The wider Hoxhunt platform uses stars, streaks and friendly competition to highlight engagement and reporting, not just “never clicking”.
A look Hoxhunt's smishing flow
With Hoxhunt, employees can report suspicious SMS messages with the Hoxhunt iOS reporting app, available on the Apple App Store. Once employees download and log in to the app, they'll simply click the native 'Report Message' link, shown when receiving a text from a new phone number.

Once reported, Hoxhunt sends a push notification telling the employee whether the reported message was a Hoxhunt SMS simulation or a potentially malicious text message.
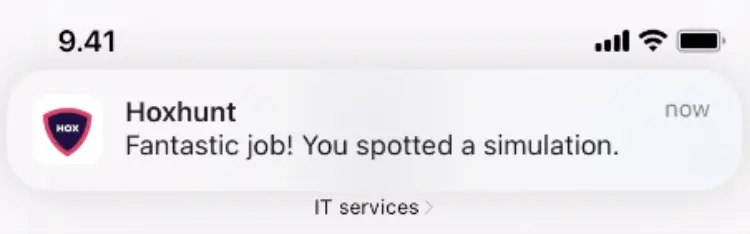
If the reported message was a Hoxhunt SMS simulation, employees earn stars for recognizing the simulated attack. Tapping the push notification opens a micro-training, allowing them to earn an additional star.
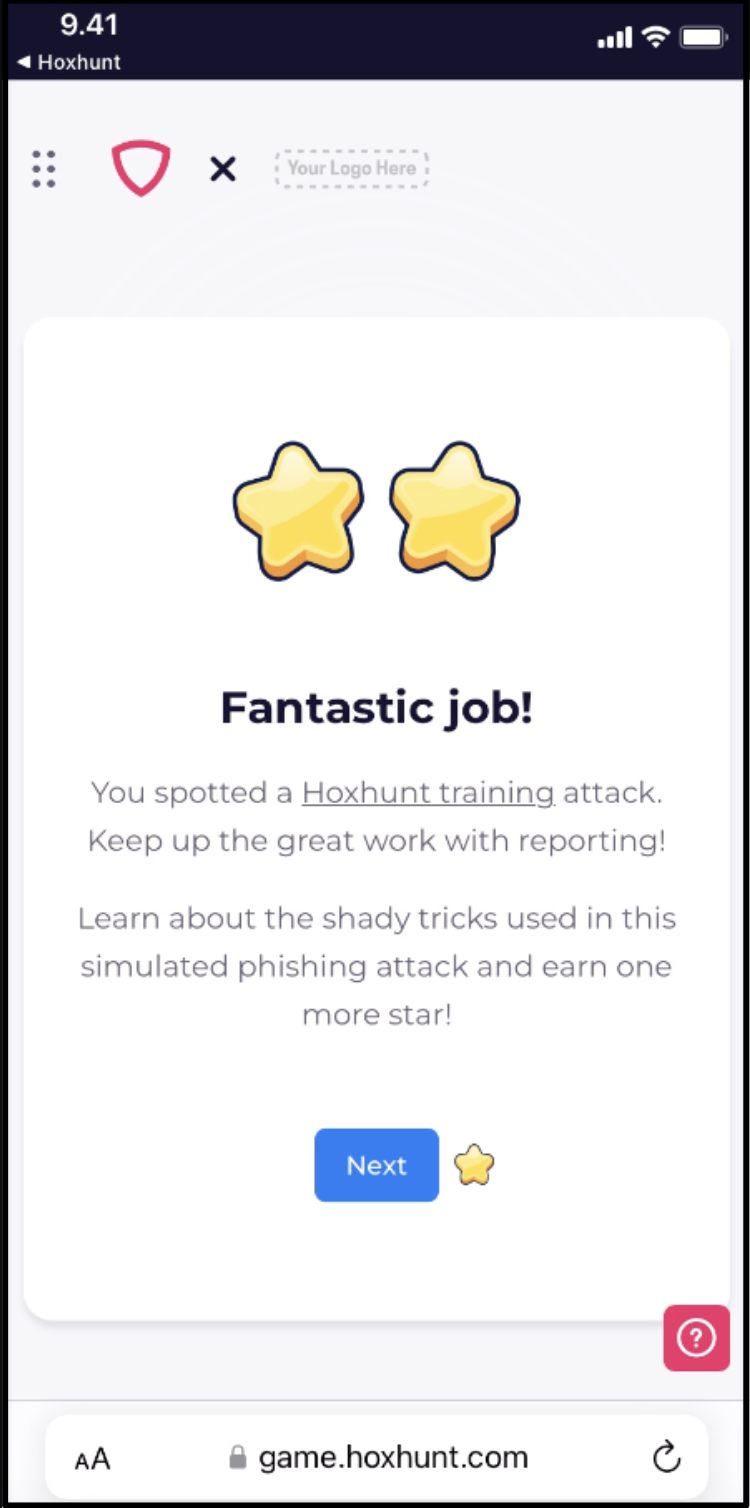
If the reported message was not a Hoxhunt SMS simulation, tapping the push notification provides the employee with an AI-powered analysis of the message, with instant feedback about potentially-malicious indicators and helpful next steps.
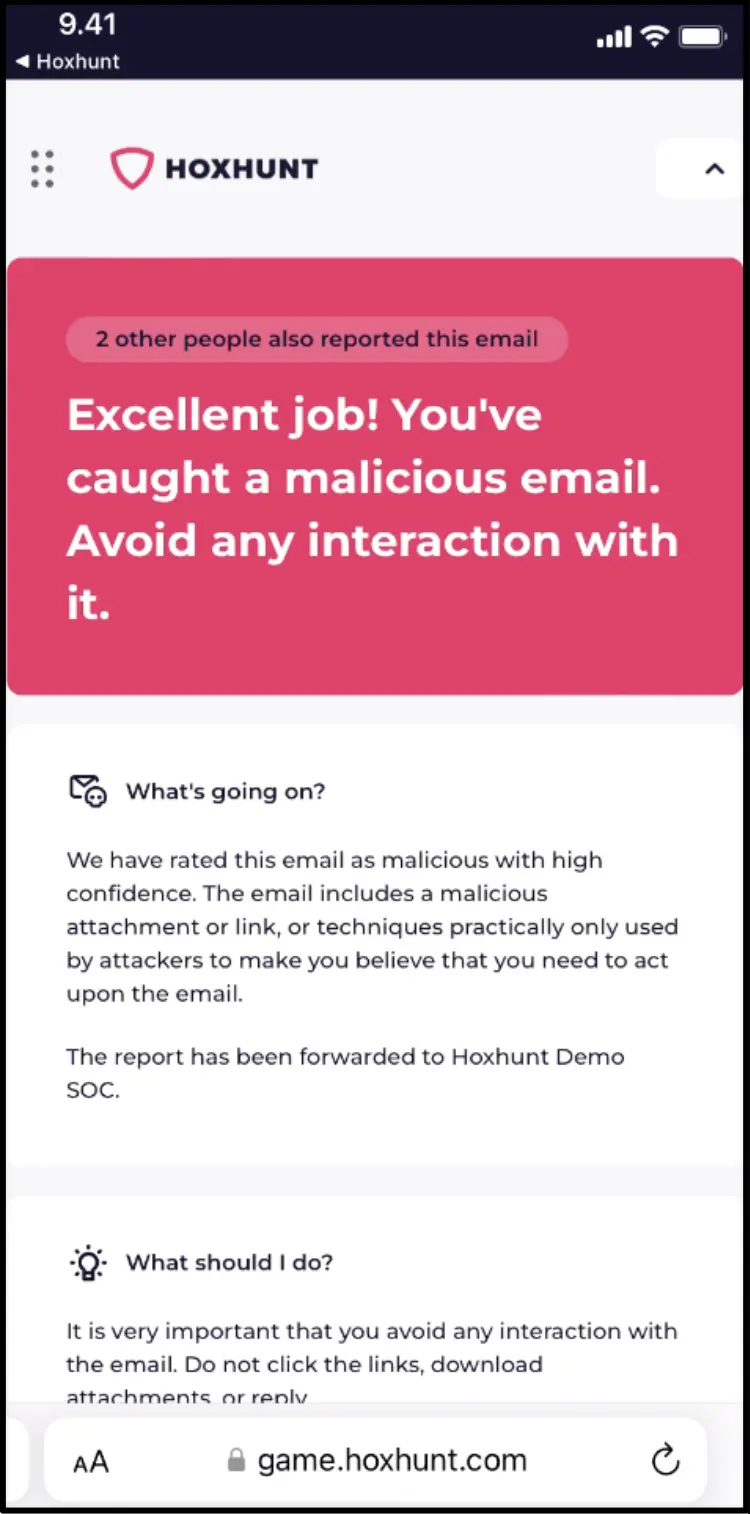
From there, all SMS user reports are logged in Hoxhunt alongside reporting analytics from other simulations and real threats, so you have a full picture of each employee's risk level and performance over time.
Keeping engagement high over time
Gamification also solves the engagement stagnation most awareness programs hit:
- Varied scenarios: smishing simulations change over time, so users don’t just memorize one template.
- Adaptive difficulty: as people get better at spotting generic lures, scenarios can become more nuanced (e.g., more convincing internal notifications) while still remaining fair.
- Recognition loops: stars, dashboards and shout-outs give managers something positive to talk about in team meetings, instead of naming and shaming repeat clickers.
How to position gamification with leadership
When you sell this internally, frame gamification not as a gimmick, but as:
- A behavior-change engine for the hardest-to-control channel (SMS).
- A way to increase reporting volume and speed from mobile devices.
- A cultural signal that you reward the right behavior instead of punishing honest mistakes.
The “game” isn’t about points - it’s about turning smishing from an invisible risk on personal phones into a visible, measurable, and even engaging part of your security program.
Smishing training for remote and hybrid teams
Smishing is hardest to manage in remote and hybrid teams because attacks land on personal phones, across time zones, and outside office networks. The fix isn’t more email training - it’s mobile-first smishing simulations, easy SMS reporting, and privacy-respecting workflows that work whether employees are at home, in a branch office, or on the move.
The remote problem in practice
For distributed teams, smishing risk is amplified because:
- Employees rely on personal smartphones for MFA, bank alerts, and work apps (BYOD).
- Security can’t see most SMS messages or easily block them.
- Smishing often arrives outside work hours, when people are distracted and more likely to click.
That combination makes judgment at the moment of the text your main control.
How Hoxhunt supports remote and hybrid environments
Hoxhunt’s smishing training is designed to work wherever people are:
- Global coverage: Smishing campaigns run in the US, Canada, and most EU countries, with regional templates that feel realistic to local users.
- Flexible provisioning: Phone numbers can be synced via SCIM or provided via CSV, so remote employees are included without manual chasing.
- iOS reporting app: Users on company or personal iPhones can report suspicious texts via the native “Report Message” link; reports go straight to the Hoxhunt platform from any location.
Micro-trainings are short and self-paced, so a remote employee can complete them between calls instead of sitting through a webinar.
Addressing privacy and trust on personal devices
Remote workers are rightly sensitive about corporate apps on their personal phones. Hoxhunt’s design helps you keep that trust:
- The iOS app does not access photos or contacts, doesn’t track location or background activity, and only processes messages the user chooses to report.
- Reported SMS are stored in the user’s Hoxhunt profile in the cloud, not on the device - so a lost phone doesn’t expose training data.
- You can distribute the app via mobile device management or the App Store, and users can uninstall it unless your policy mandates otherwise.
Combined with a clear comms plan and opt-in where required, this makes it much easier to run smishing training for remote and hybrid staff without feeling intrusive.
Best practices for deploying smishing simulations at scale
Smishing simulations work at scale when they’re legally compliant, clearly communicated, tightly segmented, and easy to report. With Hoxhunt, that means aligning legal, HR and IT, piloting with the right segments, and wrapping everything in positive, gamified coaching.
1. Get the legal and privacy foundations right
Before you send a single SMS, lock down the governance:
- Sign a smishing amendment so sub-processors and responsibilities are clearly defined; Hoxhunt requires this as a hard prerequisite.
- Respect regional limits - smishing is currently available in the US, Canada and most EU countries, but not everywhere (e.g. UK, China, Singapore).
- Collect opt-in where required. For US/Canada, you must show how employees consented (handbook, portal, mandatory training) and how they can opt out; Hoxhunt will ask for proof before ordering a toll-free number.
Transparent comms (“we will run SMS simulations, here’s why, here’s how to report”) go a long way to avoiding backlash.
2. Segment smartly instead of blasting everyone
Scale ≠ send-to-all. Use segments:
- Start with high-risk groups (finance, customer support, IT admins) or opt-in pilots before rolling out to the whole org.
- Segment by country and carrier – multi-region SMS campaigns are fragile; operators in some regions are more likely to block or rate-limit traffic.
- Use SCIM or CSV to import phone numbers cleanly (with country code, no spaces) so remote and hybrid users are included without manual chasing.
3. Design realistic, locally relevant SMS scenarios
At scale, template quality matters more than template count:
- Reuse proven patterns: delivery issues, bank alerts, payroll/tax notices, IT/O365 prompts - mapped to your real threat landscape.
- Keep SMS short and text-only, but localize brand names, language and currencies for each country.
- Avoid over-personalization that could feel creepy or cross privacy lines; at Hoxhunt we recommend not putting full names or emails in SMS content because third-party gateways may see it.
4. Control timing, volume, and monitoring
Bad timing can create more noise than value:
- Schedule sends in a defined window during working hours for each region; at Hoxhunt’ we explicitly coordinate date/time and ask the SMS provider to monitor traffic on that slot.
- Test before scale – first with internal testers where relevant, then with a small customer test group, to confirm deliverability and content expectations.
- Monitor delivery (via provider portal / API) during and after the sendout so you can react quickly if carriers start blocking messages.
5. Make reporting and feedback the hero
The goal isn’t “no failures”; it’s fast reporting and learning:
- Ensure every simulation triggers instant feedback and micro-training, so reporting feels rewarding rather than risky.
- Route real smishing reports into your threat feed and incident orchestration so SOC teams see SMS alongside email and other channels.
6. Measure behaviour, not just failure
At scale, you need simple, defensible metrics:
- Track fail rate, reporting rate, and reporting speed for smishing specifically.
- Use the data per segment (country, department, role) to decide where to focus extra coaching or where policies need tightening.
- Share positive stories: teams with high reporting rates, individuals who caught real smishing early, improvements over time.
How to implement a smishing simulation (step-by-step)
You implement a smishing simulation by defining clear objectives, targeting the right segments, choosing realistic SMS scenarios, launching in a controlled window, and then coaching users based on results. With Hoxhunt, most of this is baked into the platform - you just align legal, data, and training goals.
1. Define objectives and scope
Start with the “why” and the “who”:
- What do you want to improve: recognition, reporting, time-to-report, or all three?
- Which countries are in scope.
- Agree success metrics up front (e.g. reporting rate + reporting speed for SMS).
2. Choose audience segments
Don’t blast everyone on day one:
- Start with high-risk or high-impact groups or an opt-in pilot.
- Segment by country and carrier.
- Sync phone numbers via SCIM or CSV so remote and hybrid workers are covered.
3. Design or select SMS scenarios
Use realistic, locally relevant lures:
- Pick from SMS templates or create custom content (both are possible using Hoxhunt)
- Cover common themes: package delivery, bank/card alerts, payroll/tax, IT / Office 365.
- Keep SMS short, text-only, and localized (language, brands, currency). Avoid including full names/emails.
4. Schedule and launch
Treat the first campaign like a product release, not a one-off blast:
- Test internally (Hoxhunt uses a small US tester pool where relevant) and with a customer test group to validate content and deliverability.
- Schedule sends during work hours for each region; inform the SMS provider of the window so they can monitor traffic.
5. Capture results and coach users
The simulation is just the start, the value is in how you use the data:
- Track smishing fail rate, reporting rate, and reporting speed per segment.
- Deliver instant micro-training and stars when users report simulations, reinforcing good behavior in the moment.
- Review results by team/region and offer extra coaching for struggling groups, without naming and shaming individuals.
Which smishing simulators allow for custom text-message scenarios?
Most phishing tools were built for email, but a smaller set now support fully custom smishing simulations, letting you design your own SMS texts, short URL links, and fake login pages.
What “custom smishing scenarios” actually means
When you ask for custom smishing, you typically want to:
- Write your own SMS copy (not just use a fixed template).
- Point it to a controlled fake site or fake login page that mimics bank websites, online retailers, or SaaS apps.
- Control sender, timing, audience, and region across different mobile text messaging platforms and carriers.
- Capture who clicked the short URL link and who reported it, without routing anyone to a live phishing site.
Hoxhunt does all of this, but with an added focus on behavior change (stars, micro-training) rather than just “who failed”.
Platforms with custom SMS/text-message scenarios
Most big phishing simulation platforms (Proofpoint, KnowBe4, etc.) still emphasize email-based phishing scams and fraudulent email templates, with smishing either limited or handled via add-ons - not always with the same depth of scenario building as their email products.
Where Hoxhunt is different
Compared to generic phishing tools that bolt on SMS, Hoxhunt’s smishing module is built to:
- Fit into a broader cybersecurity awareness and human-risk program, not sit as a separate “mobile security” gadget.
- Let you design locally relevant SMS that imitate bank branches, order confirmation texts, or tax notices.
- Use every interaction (click, report) to drive micro-training and update your threat view.
Enterprise smishing simulation platform: why Hoxhunt is built for global organizations
Hoxhunt's phishing training scales from hundreds to tens of thousands of users across regions, plugs into your existing cybersecurity system, respects global regulations, and gives executives clear metrics on how smishing risk - and user behavior - are changing over time.
Built for global scale
- Geographic coverage: Hoxhunt smishing campaigns currently run in the US, Canada, and most EU countries - aligned with regional telecom and consent rules, including FCC and Federal Trade Commission requirements for opt-in.
- Enterprise provisioning: Phone numbers are onboarded via SCIM or CSV, so you can include remote staff, bank branches and frontline teams without manual tracking of account numbers or devices.
- Mobile-first: The iOS reporting app works across corporate and personal devices, turning smishing attacks on mobile text messaging platforms into visible events instead of invisible cyber threats.
Integrated with your wider security stack
Hoxhunt doesn’t replace security software, anti-malware software, or email defenses, it complements them by adding a human sensor layer:
- All reported SMS - simulations and real smishing or fake apps - flow into a central threat feed, filtered by channel.
- With Hoxhunt Respond, smishing reports are clustered and pushed into SIEM/SOAR tools.
- APIs let you export SMS events into your broader cybersecurity system, where they sit next to alerts from security apps, endpoint tools and mobile security controls.
Security, privacy and regulatory alignment
Global organizations are understandably wary of sending fake bank or tax texts to personal phones:
- Hoxhunt requires a smishing legal amendment, clear employee phone-number handling, and documented opt-in for US/Canada, in line with FCC/FTC guidance (the same rules that govern real complaint flows such as the FCC Complaint Center).
- The iOS app is deliberately data-minimizing: it doesn’t access contacts, photos, location, or other personal information; reported messages are stored in the cloud profile, reducing risk from personal data breaches if a device is lost.
Multi-language content and localized lures
For global banks, brokers and enterprises, attackers already localize phishing scams per market. So Hoxhunt mirrors that:
- Smishing templates are short, language-specific and locally themed, often using realistic short URL links and fake sites in a controlled environment.
- Hoxhunt experts help you select scenarios per country - whether that’s bank websites, Metro-style payment alerts, or fake emails and SMS purporting to fix “security updates” for popular security apps.
Reporting and C-level visibility at enterprise scale
Finally, Hoxhunt gives leadership smishing-specific metrics:
- You can track fail rate, success (report) rate and reporting speed for smishing, so you can show whether employees are getting faster at spotting and reporting SMS-based cyber threats.
- These analytics feed ROI narratives around reduced ID theft exposure, fewer successful phishing scams hitting bank accounts and account numbers, and better resilience against mobile-driven attacks that bypass traditional security patches and security updates.

Next Steps: How to prevent smishing in your organization
You prevent smishing by combining three things: clear guardrails, realistic smishing simulations, and a reporting culture where people feel safe to speak up. Technology alone can’t stop SMS-based phishing scams, so your strategy has to focus on behavior, not just filters and firewalls.
1. Set your smishing guardrails
Before you send a single simulation:
- Update policies for SMS: Spell out how employees should handle suspicious Short Message Service (SMS) texts on both corporate and personal devices, and where to report them.
- Align with legal & regulators: Make sure your approach fits FCC / Federal Trade Commission requirements for consent in the US, GDPR in the EU, and internal HR guidance so your training doesn’t look like a real cyber threat.
- Clarify “never do this over SMS”: Explicitly forbid sending passwords, account numbers, credit card information, MFA codes (e.g. from Google Authenticator), or personal data over SMS.
2. Deploy continuous smishing simulations (not one-offs)
Replace checkbox training with a rolling program:
- Run realistic, localised SMS simulations: Use Hoxhunt to send bank-style alerts, order confirmation problems from online retailers, and tax/payroll smishing that feel like real-world cyber attacks but are fully controlled.
- Cover the core red flags: Short URL link + urgency + request for sensitive data = treat as smishing. Simulations should mirror the phishing sites and fraud websites attackers actually use.
- Trigger micro-training in the moment: When someone clicks or reports, give them a 30-60 second explanation of what made that SMS risky. That “see → act → learn” loop is how you change behavior at scale.
Think of this as “always-on practice” instead of an annual exam.
3. Make reporting the hero metric
Your biggest win isn’t zero failures, it’s fast and frequent reporting.
- Give people a one-tap reporting path: On email, that’s a report button. On mobile, it’s the Hoxhunt iOS reporting app wired into the native “report message” flow on iOS.
- Reward reporters, don’t punish clickers: Use gamification (stars, streaks, leaderboards) to recognize people who report suspicious SMS and fraudulent email quickly. Avoid knee-jerk punishment that drives incidents underground and makes ID theft or personal data breaches more likely.
- Measure behaviour, not vanity stats: Track smishing fail rate, reporting rate, and time-to-report. Over time, you should see users spotting SMS-based cyber threats faster, even when they arrive through mobile text messaging platforms you don’t fully control.
4. Connect smishing into your wider cybersecurity system
Smishing shouldn’t sit off to the side as a science project.
- Integrate signals: Feed Hoxhunt’s smishing data (clicks, reports, scenarios) into your SIEM/SOAR alongside alerts from email security apps.
- Use insights to tune controls: If a cohort keeps falling for “bank text” simulations, tighten payment approvals, strengthen verification at bank branches, and double-down on training around ID Theft and credit bureaus.
- Share results up and out: Give leadership a simple story: “Here’s how fast our people now report smishing, here’s how many phishing scams we’ve intercepted early, and here’s where we’re focusing next.”
How to prevent smishing FAQs
Do we really need smishing training if we already have good email security and MFA?
Yes. Email security software, spam filters, anti-malware software, and tools like Office 365 Mail Filtering barely touch SMS text messages. Smishing bypasses those controls entirely.
Attackers use SMS phishing to grab bank account credentials, credit card information and other personal information, then monetize them via the dark web and black market. MFA helps, but SMS lures increasingly ask users for one-time codes from security apps like Google Authenticator, turning two-factor authentication into a target instead of a defence.
So the main control is user judgement at the moment of the text. That’s exactly what smishing awareness training and simulations are designed to improve.
Is it legal to run smishing simulations on employees’ personal phones?
Yes, but only with the right groundwork.
- US & Canada: FCC and Federal Trade Commission rules require documented opt-in consent for mass SMS campaigns, even if you’re texting employees on company-paid numbers. Hoxhunt requires customers to show how that consent is collected (policy, portal, training screenshot) before any campaign is sent.
- EU and other regions: Phone numbers are personal data. Local regulations and works-council rules mean it’s the customer’s responsibility to decide which numbers can be used and to obtain the necessary authorisations.
In practice, most enterprises:
- Limit early smishing simulations to corporate numbers and roles where Mobile Device Management is already in place.
- Use clear comms to explain why smishing training exists and how to report suspicious SMS.
- Offer opt-in or at least transparent expectation-setting for personal devices.
How often should we run smishing simulations without causing fatigue?
The cause of training fatigue isn’t frequency - it’s format. Annual videos and quarterly, cookie-cutter phishing tests create noise and weak outcomes; short, behavior-based micro-exercises do far better.
A practical pattern we see work:
- Light but continuous: 1-2 smishing simulations per user per month, mixed with email and other channels.
- Tiny micro-trainings: 30-60 seconds of coaching when someone clicks or reports, instead of long e-learning.
- Adaptive difficulty: More advanced users see trickier lures; newer users get simpler SMS phishing scams.
What should we do about repeat offenders who keep failing smishing tests?
Punishment backfires. Firing someone for failing a few simulations (it happens) creates fear, disengagement, and a culture where people hide incidents instead of reporting them.
Healthier patterns we see:
- Use extra coaching and targeted micro-training, not public shaming.
- Tighten technical controls around chronically risky users (reduced permissions, extra verification on high-value transactions) instead of relying on fear.
- Measure whether their reporting behavior improves over time - do they start reporting suspicious SMS and fraudulent email, even after making a mistake?
The goal isn’t perfection; it’s giving people a safe path to say, “I clicked - please help,” before a cyber threat turns into identity theft or a major personal data breach.
Will employees push back on installing the Hoxhunt iOS app or being tested over SMS?
Some will ask, “Is this app watching my phone?” That’s why design and communication matter.
- The iOS app doesn’t access photos, contacts, location, or activity; it only runs when users log in or report an SMS. Reported smishing and simulations are synced to their cloud profile, not stored locally, so a lost phone doesn’t expose data.
- Users can typically uninstall the app unless you’ve enforced it.
Paired with a non-punitive culture, this framing turns the app into a safety tool, not a surveillance tool. Employees are more likely to report suspicious SMS text messages when they trust the intent behind the program.
What kinds of SMS scenarios should we simulate and how realistic is too realistic?
CISOs want realism; HR worries about going too far. Aim for credible but generic themes: local delivery service issues, IT or HR notifications, bank alerts, order confirmation problems, without stuffing the SMS with specific personal details.
- Templates should be locally relevant (brands, language, currency) but avoid full names or emails, because third-party SMS gateways may see content and link it back to individuals.
- SMS bodies are short and text-only; shortened URLs or dynamic sub-domains can mimic how real fraud websites and fake login pages work, in a safe environment.
- You can’t reliably see delivery or read status in SMS; you mainly measure clicks vs reports, so keep scenarios simple and interpretable.
The guiding principle: realistic enough to prepare people for real SMS phishing and fraud websites, but not so personal that it feels like an attack from their own employer.
Sources
Smishing Statistics 2023: The Latest Trends and Numbers in SMS Phishing – Keepnet Labs
European Central Bank Breach: ECB Confirms Hack and Shuts Down Website – Forbes, August 2019
70% of UK Finance Industry Hit with Cyber Attacks in 2020 – Information Security Buzz, 2020
UK’s Metro Bank Hit by SS7 Attack – FinTech Futures, February 2019
Mail Disruption Creates FluBot Opening – Information Age, 2021
5 Smishing Attack Examples Everyone Should See – SecureWorld
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt




%20copy.webp)


