The best cybersecurity training programs for employees in 2026 combine phishing simulations, role-based learning, and behavioral analytics to reduce human risk measurably. Modern security awareness platforms go beyond annual compliance modules to help security teams lower phishing click rates, increase threat reporting, and track risk over time.
Below, we compare the leading cybersecurity awareness training providers used by enterprises and growing organizations, evaluated on phishing simulation depth, automation, reporting, scalability, and measurable behavior change.
Analysis is based on real reviews acorss G2, Gartner, Capterra, Reddit and more.
Why employee cybersecurity training still fails (and what to look for instead)
Human error continues to play a major role in security incidents. According to Verizon's DBIR, approximately 60% of data breaches involve the human element.
Yet many awareness programs still rely on:
- Annual compliance videos
- Static learning management systems
- Completion-based metrics
In 2026, security leaders and awareness managers are shifting from training completion to behavioral risk reduction.
That means evaluating platforms based on whether they:
- Continuously simulate real-world threats
- Adapt training by role and risk level
- Automate follow-up for repeat clickers
- Provide board-ready reporting on human risk
Top 6 best cyber security training for employees compared (2026)
1) Hoxhunt: Best for measurable behavior change & phishing risk reduction
Hoxhunt is built around human risk management. Its platform uses AI-driven adaptive phishing simulations, role-based microlearning, and gamification to produce measurable improvements in reporting rates and real threat detection.

Strengths
- Adaptive, AI-powered phishing simulations (email + multi-vector)
- Continuous microlearning triggered by real behavior
- Strong gamification (points, streaks, positive reinforcement)
- Emphasis on reporting rate and human risk scoring
- Real-time feedback when users report suspicious emails
- Enterprise-grade automation and integrations
Limitations
- Primarily focused on phishing and human risk management rather than broad compliance content libraries
- May require cultural buy-in to maximize engagement benefits
Best for: Enterpise and mid-market organizations prioritizing measurable phishing reduction, engagement, and sustained behavior change rather than compliance-only training.
2) KnowBe4: Best for broad content library & category maturity
KnowBe4 remains one of the most widely adopted security awareness platforms. It offers a large content library and frequent phishing simulations with strong administrative controls.
.webp)
Strengths
- Extensive training content
- Mature phishing simulation engine
- Established market presence
- Wide ecosystem of templates
Limitations
- Heavy email focus
- Engagement can plateau over time
- Less emphasis on individualized adaptive learning
Best for: Organizations looking for a broad, established platform with large content variety.
3) Proofpoint: Best for integrated threat intelligence environments
Proofpoint combines security awareness training with its broader threat intelligence ecosystem. The platform focuses on risk-based targeting and multi-vector simulations, particularly appealing to organizations already using Proofpoint’s email security stack.

Strengths
- Threat intelligence-informed simulations
- Multi-channel attack simulations
- Strong analytics and risk segmentation
- Integrated ecosystem advantages
Limitations
- More compelling when bundled with other Proofpoint products
- May feel suite-oriented rather than behavior-science-driven
Best for: Security teams seeking tight integration between awareness training and email threat protection.
4) Infosec IQ: Best for customizable awareness programs
Infosec IQ delivers a customizable training and phishing simulation platform with strong reporting and a wide variety of content styles.

Strengths
- Customizable content and branding
- Robust phishing templates
- Detailed reporting dashboards
- Strong coverage of compliance topics
Limitations
- Interface and reporting depth may vary in sophistication
- Adaptive personalization less central than in AI-driven platforms
Best for: Teams that value compliance alignment.
5) Cofense: Best for reporting workflow & phishing response alignment
Cofense has roots in phishing detection and response. Its training platform integrates closely with reporting workflows, helping security teams streamline suspicious email triage.
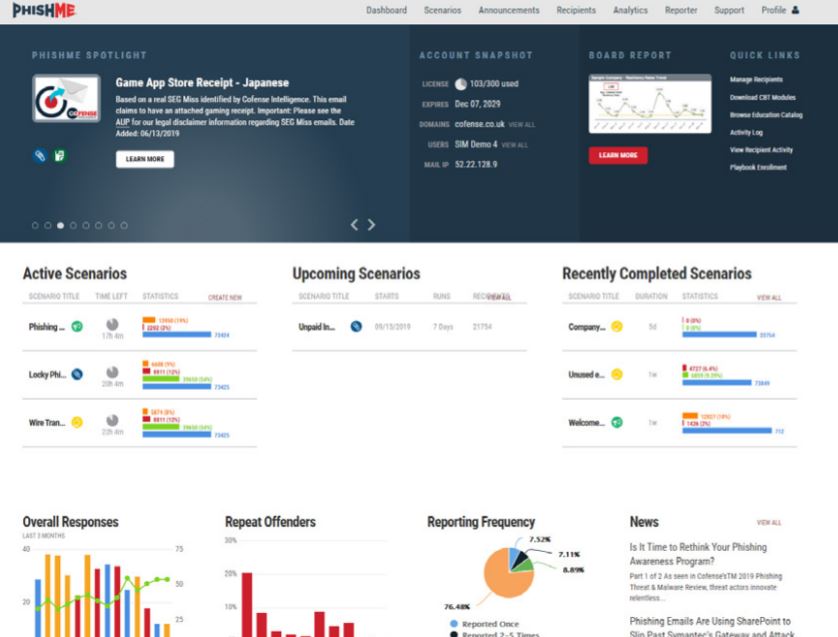
Strengths
- Strong phishing reporting ecosystem
- SOC-aligned response workflows
- Focus on real threat reporting behaviors
Limitations
- Awareness content breadth may not match category incumbents
- Engagement features less gamified
Best for: Organizations focused on improving phishing reporting pipelines and SOC coordination.
6) NINJIO: Best for story-driven awareness content
NINJIO differentiates itself with short, animated, story-based security awareness videos designed to boost engagement and retention.

Strengths
- High-quality, cinematic awareness videos
- Easy deployment
- Strong engagement for foundational topics
Limitations
- Primarily content-focused vs simulation-driven
- Limited adaptive phishing depth compared to AI-led platforms
Best for: Organizations prioritizing engaging, narrative-based awareness education.
Comparison: How these platforms stack up in 2026
Measurable outcomes: what results should you expect from cybersecurity training?
The best cybersecurity training programs for employees in 2026 are measured by behavior change.
Security leaders and awareness managers typically track five key human risk indicators:
1. Phishing click-rate reduction
Over time, effective programs reduce the percentage of employees who click on simulated phishing emails. Mature programs often aim for sustained reductions across multiple campaign cycles.
2. Increased threat reporting
A strong awareness culture increases the number of employees reporting suspicious emails or activity. Higher reporting rates often correlate with faster incident response and lower dwell time.
3. Repeat offender reduction
Leading platforms identify high-risk users (e.g. repeat clickers) and automatically assign targeted microtraining. The goal is to reduce repeat susceptibility over time.
4. Time-to-report improvement
Some advanced programs measure how quickly employees report phishing simulations. Faster reporting helps security teams contain real threats more effectively.
5. Engagement & voluntary participation
Programs with interactive or gamified elements often see higher voluntary participation rates - a signal that training is influencing culture, not just compliance.
How to choose the right cybersecurity training platform
If you manage security awareness, human risk, or compliance training, selecting the right platform depends on your organization’s risk profile, culture, and reporting requirements.
Here’s a structured framework to guide your decision.
1. Define your primary objective
Start by clarifying what you are optimizing for:
- Compliance coverage (audit readiness, regulatory alignment)
- Phishing resilience (reducing click rates and repeat offenders)
- Human risk visibility (board-level reporting and metrics)
- Security culture transformation (engagement and long-term behavior change)
Many programs fail because they try to optimize for everything at once.
2. Assess tour Risk maturity
Early-stage programs may need:
- Baseline phishing simulations
- Foundational awareness modules
- Broad employee coverage
More mature security teams often prioritize:
- Risk-based targeting
- Automated remediation for high-risk users
- Behavioral analytics dashboards
- Integration with email security and SIEM tools
3. Evaluate admin overhead
Awareness managers frequently underestimate operational effort.
Consider:
- How long does campaign setup take?
- Is phishing simulation automated or manual?
- Can training assignments be triggered automatically?
- How much customization is required to maintain engagement?
Platforms that reduce administrative load free up time for strategic work.
4. Demand measurable reporting
Before purchasing, request sample dashboards.
Look for:
- Trend analysis over time
- Repeat offender tracking
- Department-level breakdowns
- Executive-ready summary reports
If you cannot clearly demonstrate risk reduction to leadership, budget justification becomes difficult.
5. Validate with real-world feedback
Shortlist 2-3 vendors and:
- Review recent G2 and Gartner Peer Insights feedback
- Request customer references in similar industries
- Run pilot phishing simulations
- Compare engagement metrics during trials
Proof of measurable impact during a pilot often matters more than feature volume.
Decision shortcut
- If your priority is behavior-driven risk reduction, emphasize adaptive phishing and analytics.
- If your priority is compliance coverage at scale, emphasize content breadth and administrative controls.
- If your priority is integration with existing security tools, prioritize ecosystem alignment.
What makes Hoxhunt different from what you’re using now?
Behavioral science at the core
Where KnowBe4 focuses on awareness and knowledge checks, Hoxhunt is designed to shift behavior. Training evolves in response to user actions, not just policy deadlines.
We don’t tell people what to know... we train them how to behave.
This isn’t about scare tactics or finger-wagging. Hoxhunt uses motivational triggers, behavioral reinforcement, and habit formation models to drive long-term change - not just compliance box-ticking.
Truly adaptive learning paths
Other platforms talk about customization. Hoxhunt delivers it - automatically. Simulations get harder or easier based on each user’s actions. Micro modules adjust in tone and complexity. Repeat offenders are coached. High performers are challenged.
This continuous progression helps even skeptical users hit turning points. Think of these like “behavioral click moments.” It’s how we help real people in real jobs stay sharp against phishing threats and social engineering tactics.
Automated delivery - no campaigns to build
Legacy tools require manual campaign setup, targeting, scheduling, and reminders. With Hoxhunt, all of that goes away. You turn it on, configure your baseline, and it runs. Admins get out of the weeds and back to focusing on strategic cybersecurity controls.
A gamified user experience people actually enjoy
Most platforms struggle to make cyber security awareness training anything other than a chore. Hoxhunt flips that on its head.
Users get levels, badges, leaderboards, and real-time feedback - making reporting phishing emails feel more like winning, not working.
Microsoft 365 native integration
No workarounds. No risky allowlisting. Hoxhunt plugs directly into Microsoft Defender, Outlook, and Azure AD - so you get clean delivery, seamless user experience, and fewer IT tickets.
And because it’s native, threat data flows both ways, powering your detection and incident response planning, not fighting it.
Hoxhunt benchmarks
- 60% of users report at least one real threat in Year 1
- Fastest reporters flag within 60 seconds
- AES saw a 526% increase in reporting and a 79% drop in fail rate
- 6x improvement in reporting 6 months, and 86% reduction of phishing incidents.

Most teams we talk to don’t need more content. They need a platform that actually changes behavior - without turning admins into campaign managers.
Below you can see what the Hoxhunt platform actually looks like.
Best cybersecurity training for employees FAQ
What features should I look for in a cybersecurity training platform?
Key features to evaluate include:
- Realistic phishing simulation capabilities
- Role-based or risk-based learning paths
- Behavioral analytics dashboards
- Automated campaign management
- Executive-level reporting
Security leaders should prioritize measurable risk visibility over content volume alone.
How often should employees receive cyber security training?
Employees should receive continuous, bite-sized training throughout the year, not just annual modules.
Best practice:
- Ongoing phishing simulations (monthly or adaptive cadence)
- Microlearning triggered by simulation outcomes
- Role-based refreshers for high-risk teams
Annual training alone is insufficient for evolving threats.
How long should security awareness training take?
Modern training is built around 2-5 minute microlearning modules, delivered contextually.
Long, 45-minute sessions reduce retention and engagement. Short, frequent reinforcement - especially after a simulation - improves behavior change and reporting habits.
What is a good phishing click-rate benchmark?
Initial phishing click rates commonly range from 10–30%, depending on industry and prior training maturity.
Well-run programs typically aim to:
- Reduce click rates below 5%
- Increase reporting rates significantly
- Shrink repeat-failure cohorts over time
How long does it take to see measurable improvement?
Most organizations see measurable trend changes within 60-90 days when simulations and microlearning run continuously.
Early indicators:
- Reporting rates increase
- Repeat offenders decrease
- Click-rate trends decline
Long-term impact depends on consistency and adaptive difficulty.
Sources
Hoxhunt - Gartner Peer Insights, G2 Reviews, Capterra Reviews, TrustRadius Reviews
Proofpoint - Gartner Peer Insights, G2 Reviews, Capterra Reviews
KnowBe4 - Gartner Peer Insights, G2 Reviews
Infosec IQ - Gartner Peer Insights, G2 Reviews
Cofense (PhishMe) - Gartner Peer Insights, G2 Reviews, FeaturedCustomers
NINJIO - Gartner Peer Insights, G2 Reviews
Standards & Guidance - CISA Phishing Guidance, NIST Security Awareness and Training (SP 800-50)







