2025 Threat landscape overview: persistent social engineering tactics
The phishing playbook hasn’t changed - but the pages are being rewritten. Attackers continue to rely on tried-and-true social engineering tactics, but in 2025 these methods show sharper execution, new twists and even AI-powered polish.
Microsoft remains the most impersonated brand, with attackers exploiting different emotional triggers, such as urgency or curiosity. Phishing attacks also share fake documents and impersonate well-known services like Docusign to seamlessly blend into everyday workflows.
Some of the most popular 2025 campaigns impersonated HR departments, luring employees with promises of salary increase lists or bonus plans. Others campaigns utilize supply chain lures, with attackers even compromising real company email accounts to amplify credibility.
What makes these campaigns effective isn’t just the content - it’s the emotion.
Attackers consistently exploit:
- Urgency (security alerts, expiring access)
- Curiosity (documents, voicemail transcripts)
- Trust and authority (HR, suppliers)
- Reward-seeking (bonus lists, pay raises)
The end goal remains the same: the threat actors aim to compromise organizational accounts.
Table 1: Most Targeted Industries: 2024, 2025
Note: These industry threat figures only indicate attacks that have bypassed filters and penetrated email inboxes. Figures are derived from harmonized threat reporting rates in the simulated and real email environments, a fundamental departure from filter-level attack data. The most important attacks for human risk management purposes are those in inboxes and thus actually pose a threat to users.
It’s possible that some industries that are heavily targeted, e.g. Finance, have stronger filtering technologies and firewalls in place, along with overall greater levels of security maturity. Those differences in security posture between industries may account for the fluctuations in attacks, both targeted and mass campaigns.
🧭 Insights
- Manufacturing remains the most targeted industry by volume, despite a –27.6% decline in malicious messages reaching inboxes.
- Oil & Energy climbed 8 ranks to become the fastest-rising target, with both exposure and click likelihood more than doubling.
- Pharma & Healthcare also surged, confirming its place among 2025’s highest-risk sectors.
- Education dropped 5 ranks—the largest decline.
- IT dropped 3 ranks.
Table 2: Malicious Click Reduction: Standard SAT vs. Hoxhunt
Explanation of the data on the projected malicious clicks and risk reduction
Hoxhunt projects the number of malicious clicks per user by harmonizing simulated phishing reporting and failure rates with real threat reporting rates. Global simulated reporting rates with Hoxhunt users can exceed 60% of the dozens of simulated phishing attempts per year in the training environment. We predict with strong statistical confidence that real reporting rates will thus signify a similar percentage of the total threats.
So, if there were 0.087 malicious threats reported per user in 2025 in the manufacturing industry, with a 64% simulated threat reporting rate, we can extrapolate that those 0.087 reports represent only 64% of total threats. To determine the total number of threats in that industry, we divide 0.087 by 0.64, yielding approximately 0.136 threats per user. In a 1,000-user organization, that equates to about 136 malicious threats reaching inboxes annually.
Benchmark tests involving hundreds of thousands of users globally have found that the simulated failure rates of users in standard SAT is roughly 20%. It is, conservatively, about 4% with Hoxhunt after 6 months of training, but it varies from company to company and from industry to industry. The projected malicious clicks per user, and per 1,000-user organization with and without Hoxhunt, is based on how many real threats are likely clicked on in an org with a 20% failure rate compared to Hoxhunt-users' industry failure rate.
66% of Hoxhunt users report one threat within 1 year of beginning training.
By harmonizing simulated and real threat reporting environments and user behavior, Hoxhunt predicts real threat and real threat reporting incidence between different cohorts as no other data set to our knowledge ever has.
Microsoft vs Google environments
Campaigns reported from Microsoft environments versus Google environments showed some variation and some similarities. Microsoft impersonations were more common in Microsoft environments, while Google impersonations were not common in either environment.
Users of Google environment reported more Docusign impersonations, while users of Microsoft environments reported more HR-related threats. Users of both environments reported business email compromise-related third-party impersonations and fradulent supplier offers.
Generative AI has changed the look of phishing emails
The prevalent use of AI is making phishing messages appear more polished and professional. (Yet our Hoxhunt analysts find that a “glossy” look doesn’t always make phishing more convincing. In some cases, simpler phishing emails still appear more legitimate).
Attacks targeting specific industries and regions
While phishing is still mostly global and opportunistic, targeted attacks and attack patterns are sometimes observed. For example, QR-code lures stand out in retail, where QR workflows are familiar, and voicemail phishing is more commonly observed in North America than in other regions.
These trends suggest that while attackers lean on universally effective tactics like Microsoft alerts or file-share requests, they occasionally tailor their campaigns to the cultural, technological, and business realities of their targets.
The bottom line
Our threat intelligence tells us that phishing continues to thrive by leaning into emotional triggers, familiar workflows, and globally recognizable brands. Threat actors are basing their attacks on proven social engineering tactics, but some things do stand out as a distinct feature of 2025 - such as SVG files and their rising popularity.
What are SVG phishing email attachments?
SVG (Scalable Vector Graphics) is a popular web image format that stays crisp and clear at any size, making them great to use on websites and emails. But beyond just pictures, these files can contain hidden malicious code, links and interactive elements. This allows attackers to hide content inside SVGs, and trick users to loading malicious files or redirecting them to fake login pages. Disguised as harmless graphic files, SVG files often slip past email security filters.
Why attackers use SVGs
- Often misclassified as “just images.” Many gateways allow SVG by default and don’t deeply parse them.
- Obfuscation-friendly. Payloads hide in
data:/Base64 blobs, styles, unusual attributes, or nested elements like<foreignObject>withonloadhandlers. - Redirect-friendly. Links buried in
xlink:hrefor DOM-injected HTML can evade simple link rewriting and jump to credential pages.
How prevalent are SVG phishing email attachments in 2025?
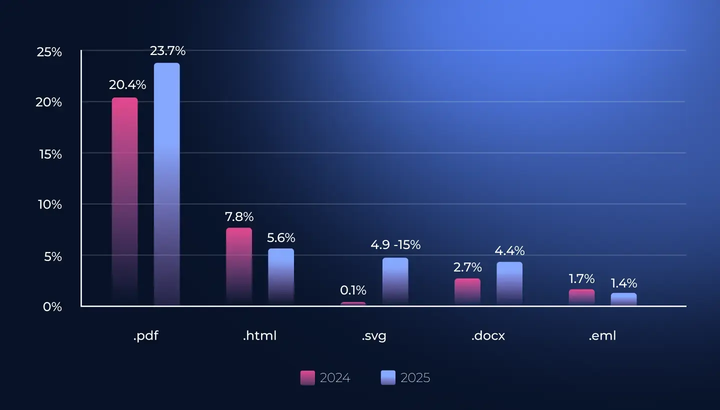
Attackers are increasingly using SVG files in their campaigns: in fact, 2025 saw an explosion in their usage. In 2024, the use of SVG files was a very niche technique, making up only 0.1% of all attachment-based phishing reported to Hoxhunt. They were far behind more common attachments like PDFs, HTMLs and Microsoft Word Documents.
However, in 2025 - while still behind the PDFs - SVGs are the most popular and versatile file type. SVGs have almost caught up to HTML files and surpassed DOCX-files. By the beginning of July of 2025 SVG files made up 4.9% of all observed attachment-based phishing, and March 2025 saw a peak of a whopping 15% (Figure 1).
Figure 1. The proportion of SVGs in all attachment-based phishing from July 2024 to June 2025.
Comparatively, Figure 2 shows the Top 5 attachments used in phishing in H1 2025, and their shares in 2024. PDF attachments made up 23.7% of all attachment based phishing in H1 2025, HTML attachments made up 5.6%, DOCX-files made up 4.4% and EML attachments 1.4%. In 2024, PDFs made up 20.4% of all attachment based phishing, HTMLs made up 7.8%, DOCX-files made up 2.7% and EMLs 1.7%.
How an SVG phishing attachment works
A typical SVG phishing campaign starts with a lure, delivers a small .svg attachment or hosted download, then uses embedded scripts and encoded data to redirect the browser to a look-alike page. Because many secure email gateways treat SVGs as images, link-rewriting and static checks miss the phishing URL.
Real SVG threat breakdown (step-by-step)
1) Email lure
In the real-life example we'll look at below, threat actors used a document share lure, claiming that the recipient had received a secure document related to salary benefits from payroll. This type of social engineering, where attackers exploit emotions such as curiosity or authority, is nothing new. Here, the attackers also embedded a malicious hyperlink in the email which is still one of the most common methods of delivering phishing payloads.

2) Hosted file
However, the link led to ShareFile, where the recipient was urged to download an SVG file.
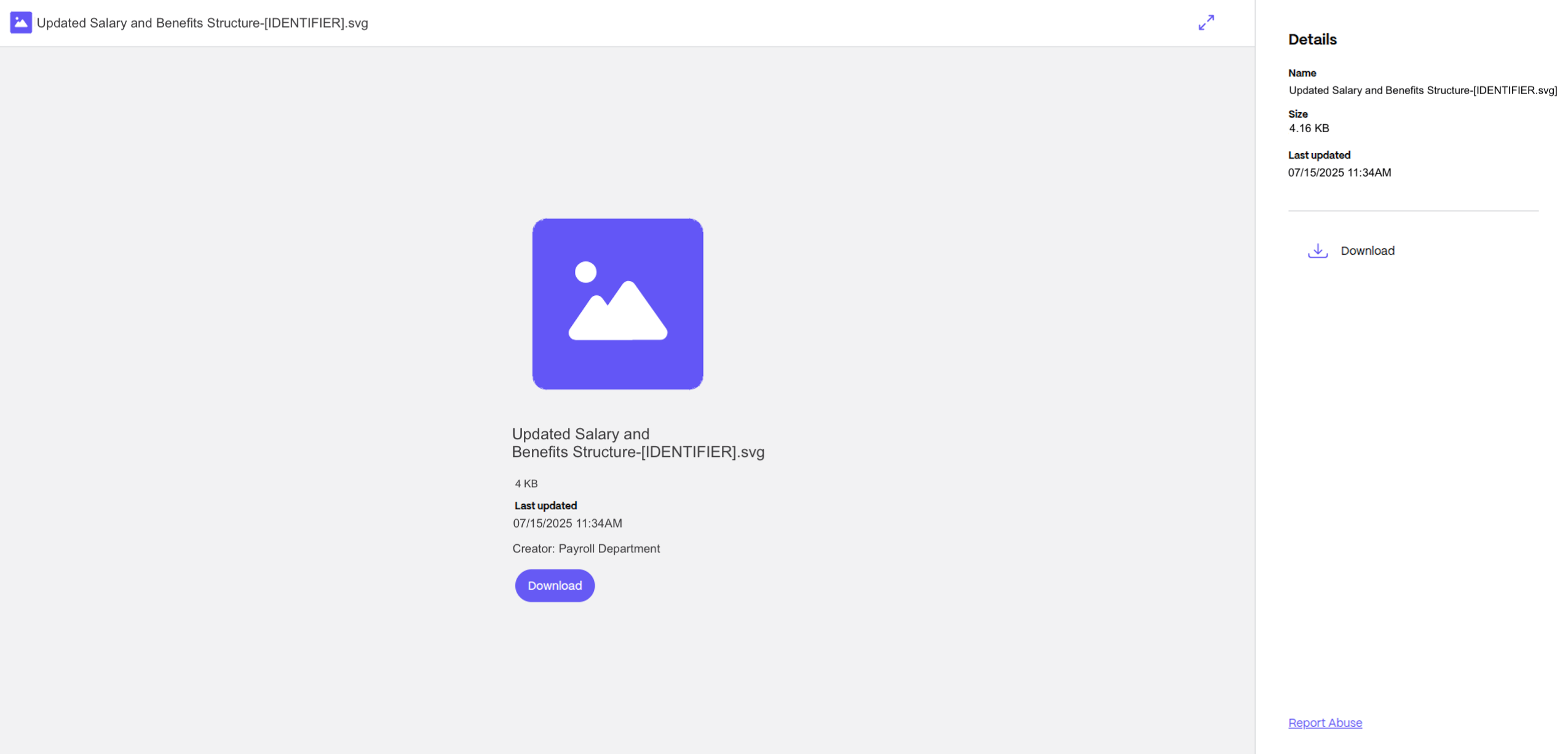
3) SVG prompt
When downloaded, the SVG file prompted the recipient to type in the password provided in the email.

4) Credential harvesting
Upon entry, the recipient was taken to a Microsoft credential harvesting page.

Why it bypassed filters
- Often misclassified as “just images”, which is why many email gateways allow SVGs.
- Obfuscation hides intent. Attackers bury links in unusual attributes, base64/data URLs, styles, or nested elements that basic link-rewriting doesn’t catch.
The use of SVGs and even third party services like ShareFile shows that while the bulk of phishing still relies on familiar lures like Microsoft alerts or fake documents, attackers are experimenting with new delivery methods. While certain themes persist, the threat landscape is ever-changing.
SVG attachment phishing mitigation checklist (enterprise)
SVG phishing is mitigated by treating SVG as active code, not an image: Block or quarantine attachments, sandbox-render to catch embedded scripts/Base64 redirects, harden Microsoft 365/O365 and Secure Email Gateways, and train employees to prefer PNG/JPG.
Policy
- Treat SVGs as active content, not benign images.
- Consider blocking or quarantining SVG attachments, and allow PNG/JPG for email imagery.
- If truly required for business, limit to a sanitized SVGs delivered via trusted channels.
Filtering / analysis
- Run SVGs in a safe sandbox to render them and log any redirects or downloads.
- Treat .svg as high-risk; block or detonate pre-delivery.
- Flag SVGs containing <script>, <foreignObject>, onload, xlink:href, data:/Base64 encoding, or suspicious DOM manipulation APIs.
- Rewrite and expand phishing URLs/redirect URLs inside data: URIs; follow through to detect phishing webpages and kits.
Email authentication & posture
- Enforce DMARC with SPF/DKIM alignment (quarantine→reject), especially for executive domains used in business email compromise.
- Rate-limit or block inbound mail from newly observed domains and free-mail signups when sent in bulk to many email addresses.
- For IMAP clients, disable auto-downloading/preview of attachments.
Microsoft 365 / browser hardening
- In Microsoft 365, disable HTML/JS rendering in previewers where configurable; restrict side-loading of file viewers.
- Use Microsoft Edge or a managed browser with download protection and isolation (Application Guard/VDI) for opening unknown attachments.
- Apply strict safe links and safe attachments for all users; create a VIP policy for high-risk roles.
Monitoring & incident response
- Create a playbook: “Opened an SVG” → reset password, revoke sessions, check mailbox rules/forwards, and scan endpoints.
- Hunt for recent browser launches of .svg followed by POSTs to unfamiliar domains or Telegram Bot API beacons.
- Track “first seen” SVG hashes; pivot on senders and phishing campaigns that reuse phishing kits.
Awareness training
- Train employees that an SVG file that’s anything more than an image is suspicious and should be reported.
- Include a 60-second micro-module: “SVG ≠ image.” Show how embedded scripts/Base64 can redirect to a fake Microsoft 365 login.
Red flags to watch out for
- An SVG file that opens up a web page, prompts a download or asks for credentials.
- Unexpected .svg attachments, especially from untrusted senders.
- ShareFile/DocuSign/HR themes asking you to download a tiny “image” that later requests a password.
- Files that open with browser prompts, pop-ups, or multiple redirects before showing content.
Defense strategies for your employees
- If you must view an image and it’s SVG, ask the sender to convert it to PNG or send over the information another way.
- If an SVG-file is interactive in any way, close it and report it. Do not enter passwords.
- When in doubt, navigate directly (manual URL or official app) instead of clicking the attachment link.
- If you clicked, report immediately; do not retry or “test” the link again.
QR codes are waning in popularity
In 2023, we reported a surge in QR code phishing, when their usage in malicious emails shot up from negligible numbers to over 20%. Where are we two years later?
The answer is: in a better place, since in H1 2025, QR codes were only detected in under 2% (0.7%-2%) of malicious emails. But that’s not the whole truth. Data combined with analyst domain expertise confirms that use of QR codes has decreased, mostly due to better email filtering. However, attackers are now hiding QR codes in attachments, making it harder to analyze their popularity.
The moral of the story is that back in 2023, the popularity of QR code phishing exploded because using them was an easy way for attackers to bypass email filters. Since email filters have caught up and improved defenses against malicious QR codes, attackers are now using them less or hiding them in attachments.
There might be a lower volume of malicious QR codes out there, but they still exist and are just as malicious as before. So unless you know they’re safe - don’t scan.
We compared emails reported by users of Microsoft environment and those reported by Google environment users. Here’s what we found.

Threat reporting accuracy, Microsoft vs Google
We compared emails reported by users of Microsoft environment and those reported by Google environment users. Here’s what we found...
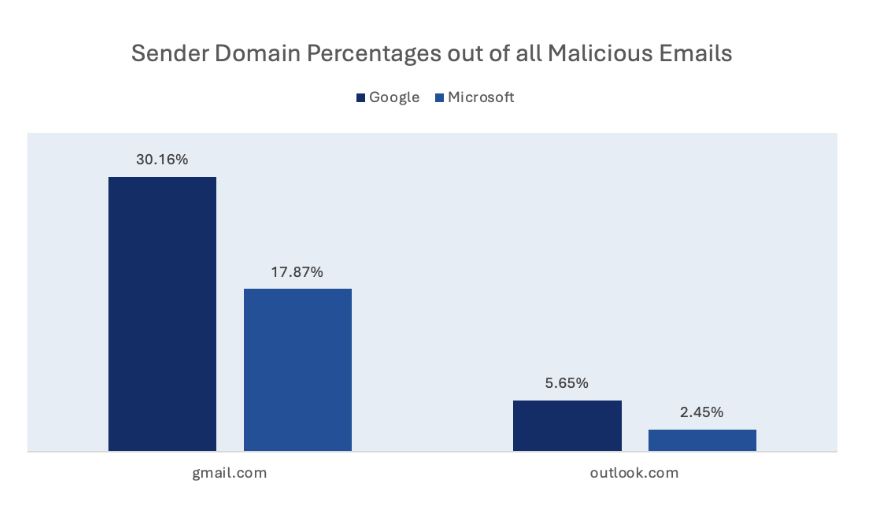
During 2025, out of all emails reported as threats by Google environment users, 12,1% were malicious. For Microsoft environment users, the number was 34,7%. This could be the result of factors such as the different spam filtering solutions employed by these environments, variance in phishing campaign types between the environments, and variance in user tenure and reporting skills.
Sender domain insights
The most common sender domain that malicious emails came from was “gmail.com”, and the second most common was “Microsoft Outlook Personal Email and Calendar | Microsoft 365 ” in both environments.
The top domains observed in the Microsoft environment included other very common domains like:
- “Microsoft Outlook Personal Email and Calendar | Microsoft 365 ”
- Third party services like “Docusign Account Login | Sign in to Docusign ”
- And “Salesforce: The #1 AI CRM ”.
In the Google environment on the other hand, more campaign-specific domains were trending, potentially due to better filtering of large bulk-phishing campaigns.
The most common malicious top level domains were very similar in both environments. The most common ones were “.com”, “.net” and “.org” in both environments.
A top-level domain (TLD) is the suffix that appears at the end of a web or email address - such as “.com” in “Google ” It indicates the website’s category (for example, commercial, governmental, educational) or its geographic origin.
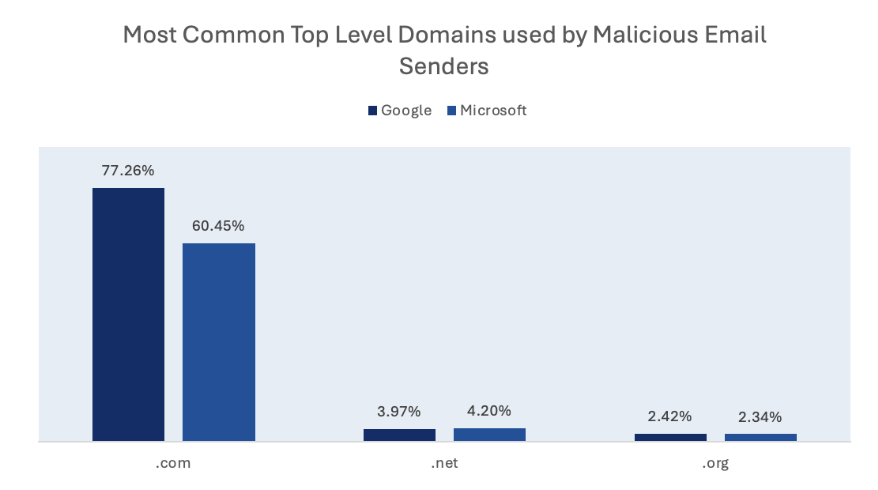
Environment specific campaigns
When diving deeper into the content of threats sent to each environment, we discovered the following patterns:
Reports show a split by environment. Microsoft tenants most often saw Microsoft-themed impersonations and more internal HR spoofs (salary/bonus lures). DocuSign impersonations were reported more frequently in Google environments. Microsoft tenants also received brand-agnostic document-signing lures, while Google-impersonation lures were uncommon in both environments. Differences likely reflect targeting and/or filtering variation, not absolute absence.
Users of both environments reported BEC-related third-party impersonations, fraudulent supplier offers, and fake wire transfer receipts.
Cyber threats by industry rankings
Top entities impersonated:
- Microsoft
- Human resources
- Supply chain third parties
Top emotions exploited:
- Urgency
- Curiosity
- Trust
- Approval
- Reward-seeking
About Hoxhunt: training that changes behavior
Hoxhunt turns real-world threat intelligence into teachable moments. Our platform analyzes reported threats monthly from +3 million users, then personalizes phishing training and simulations (including SVG and QR code lures) inside Microsoft 365 and Google environments. The result: higher report rates, fewer risky clicks, and faster incident response.
What we do
- Deliver adaptive security awareness training (SAT) that mirrors live phishing attacks and phishing campaigns.
- Embed training/reporting where people work (Outlook/Microsoft 365, Gmail), with one-click reporting from the email client.
- Automate personalized simulations at scale, so that every user's training path is relevant to their location, rile and skill level.
Why it works
- Uses current, customer-reported cyber attacks to keep lures relevant.
- Personalized challenges that raise report rates and reduce risky interaction with phishing webpages and phishing URLs.
- Integrates with enterprise controls to reinforce your program.
- Reduces noise, eliminates org-wide threats by automating your SOC busywork with AI-powered detection and analysis that resolves false-positive reports and categorizes incidents.
What outcomes to expect
- 20x lower failure rates
- 90%+ engagement rates
- 75%+ detect rates
Below you can see what Hoxhhunt training looks like for your end users.
SVG phishing email attachments FAQs
Is it safe to open an SVG from email?
No. Treat SVGs as active content and prefer PNG/JPG.
What if I opened a SVG phishing email attachment?
If you clicked or typed crendentials: notify SecOps, follow their instructions and reset password.
Do phishing emails include attachments?
Yes:. PDFs, HTMLs and SVGs are common. They can hide links and credential harvesters or trigger downloads.
Should you use SVGs in email?
Avoid SVG attachments, use PNG/JPG instead.
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt




.webp)