Threat actors are targeting hotel staff with booking-related phishing emails and the ClickFix social engineering technique. These phishing campaigns are some of the most commonly observed examples of industry-specific targeting across the Hoxhunt network.
This article examines why hotels are targeted, how booking-related phishing campaigns operate, the operational and financial impact on hospitality, and what awareness teams can do to reduce human risk.
Why are hotels prime targets for cyberattacks?
The accommodation industry handles a high volume of sensitive customer data, from payment card data to passport numbers and contact details. This makes breaches highly profitable for threat actors looking to extort the breached company, or sell data on cybercrime forums.
Operational disruptions impact both revenue and guest experience because guests depend on working check-in, room access, and payment systems, thereby increasing ransomware leverage. Time-sensitive scenarios such as cancellations and other last-minute changes, combined with reliance on third parties like booking platforms, create natural pretexts for social engineering.
Observed phishing campaigns targeting hotels (OTA impersonation + ClickFix)
Attackers target the accommodation industry using multiple angles, impersonating both guests and online travel agencies (OTAs) such as Booking.com.
These campaigns have been observed across the Hoxhunt network in recent months and reflect active, ongoing targeting of hotel staff.
Campaign 1: Booking request pretext → ClickFix
The first example campaign begins with a booking request, often for a larger group such as a construction crew or a sports team. Larger groups might often coordinate bookings via email instead of through standard booking platforms, which makes the initial email seem more legitimate. These emails are usually sent from free email addresses, most often from gmail.com. The visible sender names are often different from the local-part (the part before @) of the gmail address: the sender name might show as “Name_1”, while the email is [Name_2]@gmail.com.
Apart from the sender-local-part mismatch, the individual initial contact requests are not overtly suspicious. However, the attackers are bulk-sending emails that tell the same story with some slight variation in details and wording, potentially suggesting AI-assisted drafting. While individually the emails might look benign, volume reveals a pattern.
If the recipient answers to the booking request, they receive a follow-up email. Threat actors claim they have seen negative reviews, related to, for example, extra fees or reported thefts, and share a malicious link that seems to lead to Booking.com (Figure 1).

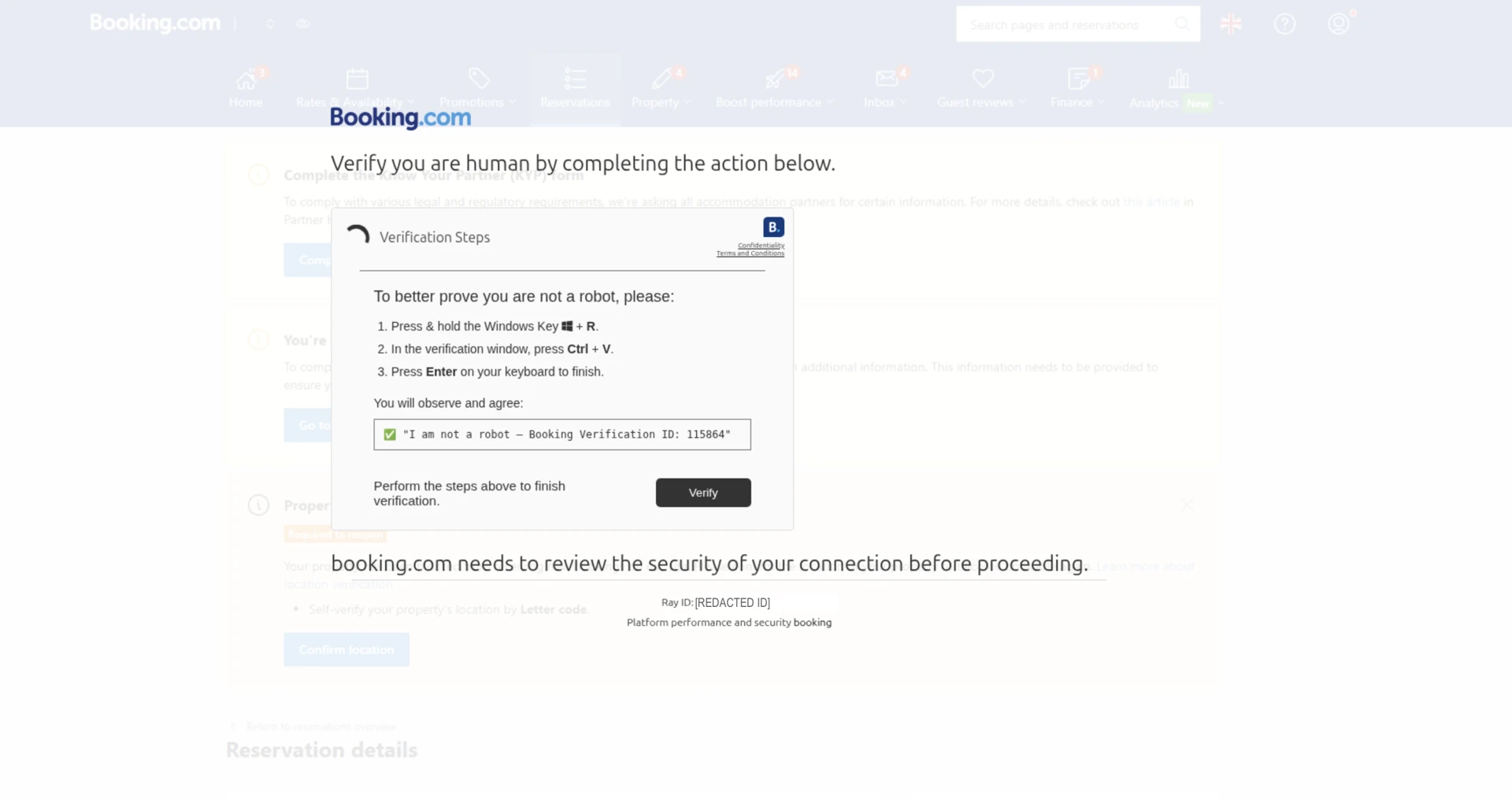
In reality, the link leads to a malicious lookalike Booking.com site. The landing page first prompts the recipient to verify they’re human by completing a fake CAPTCHA, and claims the site needs to review the security of the recipient’s connection (Figure 2). Next, the user will be shown a series of commands they need to complete to “finish verification” (Figure 3). This is an example of the ClickFix technique, where threat actors' goal is to trick users into running malicious commands themselves.

Campaign 2: Booking.com impersonation → ClickFix
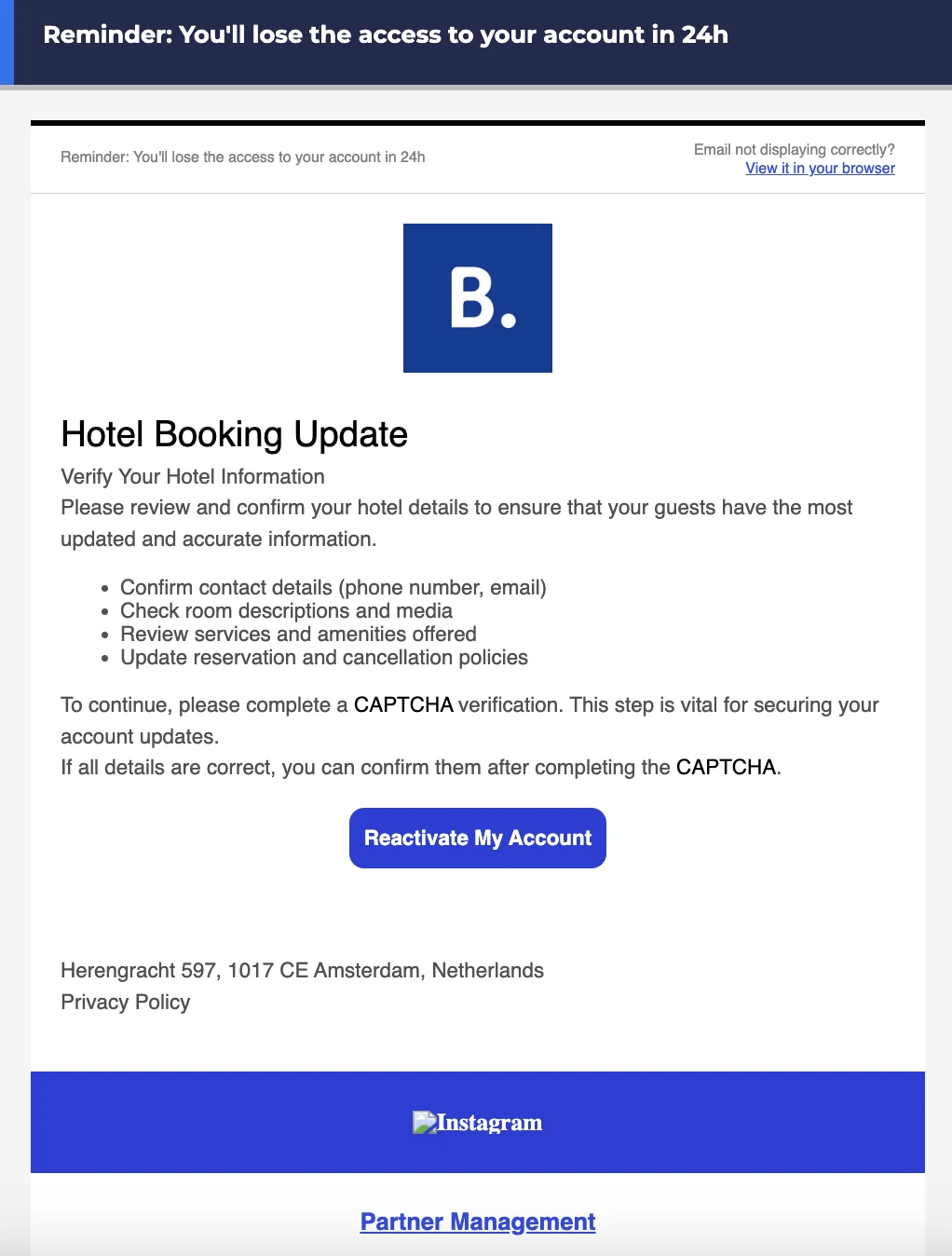
In the second campaign, attackers directly impersonate Booking.com, claiming the recipient needs to confirm hotel details to reactivate their account (Figure 4). If the first example relied more on regular workflows, this campaign leans on urgency and fear, as the email claims the recipient will lose access to their Booking.com account within 24 hours. The phishing email requests the recipient to complete a CAPTCHA verification, which suggests the landing page of the campaign may also use the ClickFix technique.
The common denominator: Booking.com and ClickFix
These campaigns show that as of early 2026, attackers are actively targeting the hotel industry with Booking.com lures and ClickFix. In January, researchers detailed how Booking.com impersonations and ClickFix are being used to deliver DCRat malware, which allows for persistent remote access, password theft and collection of other sensitive information.
ClickFix takes advantage of the recipient’s willingness to quickly resolve a problem themselves, especially under seeming time pressure. Many hotels rely on Booking.com for visibility and operations, meaning losing access to the account even momentarily could have a significant impact on business.
You can read our full phishing trends report here, covering the latest threats bypassing filters and what's working when it comes to training programs.
How cyberattacks hit hotels (and where it hurts first)
After successfully infecting a computer with malware or gaining access to systems via credentials, the attackers can do significant harm to operations and confidential data. The consequences, whether financial, human or reputational, might be serious, as is evident from the following example.
In 2025, a casino hotel company paid $45 million to affected customers of a 2019 data breach and 2023 ransomware attack to settle multiple class action lawsuits. According to the company, the ransomware attack resulted in approximately $100 million in losses due to disrupted operations and other expenses like legal fees. These costs show how cyber incidents can compound over years through litigation, remediation and lost business.
During the incidents, sensitive customer data, like names, addresses, passport numbers and social security numbers was leaked. The exposure of this type of data has long-term risks for those affected, such as identity theft or further targeted phishing attempts. Following the ransomware attack, the company took some of its systems down and there were reports of slot machines, ATMs and room cards not working. This means the attack directly damaged customers' trust in the company’s ability to not only safeguard their data, but also ensure their safety on-site.
Reducing hotel phishing risk: awareness behaviors and security controls
Awareness behaviors
- Ensure security awareness training for front desk staff covers booking platform impersonations, fake customer requests and ClickFix technique.
- Emphasize “pause-and-think” before clicking links. Rather than clicking, employees should be advised to navigate to booking platforms and other systems via official domains.
- Encourage end users to report real suspicious emails and other suspicious behavior through simple reporting flows and positive feedback. Employees should feel comfortable reporting even after a click or command execution.
Security controls
These controls limit damage but they don’t prevent initial compromise on their own - especially in booking-driven phishing attacks.
Ensure typosquatted and newly registered domains are quarantined or flagged, and quarantine emails with URLs that redirect multiple times.
Protect your systems from ClickFix:
- Reduce user ability to run commands or scripts.
- Review PowerShell execution policies to prevent abuse.
- Enable PowerShell Script Block Logging to detect malicious activity.
What should hotel staff do when they receive an OTA or booking message?
In busy hotel environments, staff don’t have time to analyze every message. What works in practice is a clear, repeatable response that can be applied consistently during peak check-in and other high-pressure moments.
The default response for booking and OTA messages:
- Don’t act inside the message. Don’t click links, open attachments, follow “verification steps” or copy commands.
- Verify via the known path. Open the OTA or booking platform using a saved bookmark or official domain and check there.
- Report immediately. Escalate suspicious messages even if you’re unsure, or after a click.
When this response is working, ‘zero clicks’ isn’t the only metric: the measurable impact is faster reporting and better visibility into suspicious booking and OTA messages, letting teams respond before issues spread.
How awareness teams operationalize this in hotel environments
Awareness teams don’t need to introduce new concepts for each campaign. The goal is to apply the same response consistently across onboarding, simulations, and when coming across real phishing emails.
Brief, regular reinforcement works better than infrequent long-form training. Short simulations and reminders tied to booking workflows keep expectations clear without disrupting operations.
Make it part of onboarding
High turnover means phishing risk resets frequently. Effective programs introduce realistic simulations early, using examples staff are likely to encounter on shift.
- Day 1: Explain the default response and reporting path.
- First weeks: Reinforce the same response with realistic booking-themed simulations.
- First month: Repeat the scenario with small variations while keeping expectations unchanged.
The goal is to prioritize familiarity over mastery
Standardize across properties
For multi-property or franchise environments, consistency is key:
- One response pattern for booking-related messages
- Role-relevant examples for front desk, reservations, and finance
- Regular review of reporting and response trends to spot gaps
This keeps teams aligned while allowing staff to focus on guest service.
Metrics that matter for hotel phishing risk (how awareness teams prove real impact)
Hotel awareness programs succeed when they can show measurable risk reduction without relying on vanity metrics like completion or click-rate alone. The most reliable signal is whether frontline staff report suspicious booking/OTA/vendor messages quickly and consistently. These four metrics translate directly into better detection, faster containment, and board-safe progress tracking.
The 4 metrics to track
Hoxhunt for hotels: reducing booking-themed phishing risk without slowing front-desk operations
Hoxhunt helps hotels apply the guidance outlined above at scale by offering realistic booking- and OTA-themed simulations, making reporting easy for frontline teams, and giving security leaders clear visibility into reporting behavior and response speed.
Train the scenarios hotels actually face
Hoxhunt campaigns can mirror the real pretexts shown in this guide - booking inquiries, guest complaints, account reactivation pressure, and fake verification prompts - so training feels like the job rather than generic security content. That matters in hospitality because relevance is what makes learning stick, especially for new hires and frontline roles.
Make reporting the “default action,” even after a mistake
Hotels don’t need perfection, they need speed and visibility. Hoxhunt’s approach reinforces reporting as the right behavior, including when someone clicked or followed steps, because fast escalation is what allows response teams to contain damage. Punitive programs suppress reporting; supportive programs increase it.
Reduce admin overhead for lean hotel security teams
Hotel security and IT teams are often stretched across multiple properties. Hoxhunt is designed to reduce manual campaign management - setup, follow-ups and ongoing maintenance - by running continuous training, so you can focus on trends, high-risk areas, and specific cohorts (front desk, reservations, finance) instead of endless scheduling.
Prove improvement with metrics leaders understand
Completion rates and click rates alone can be misleading. Hoxhunt emphasizes reporting- and speed-based measurement, so awareness managers can show progress in the outcomes that matter operationally:
- Reporting rate (are staff escalating suspicious booking/OTA messages?)
- Time-to-report (how quickly does the first report happen?)
- Miss rate (how often are suspicious messages ignored?)
Below you can see how Hoxhunt maximizes user engagement with personalized simulations at scale.
Key takeaways for hotel security and awareness teams
- Hotel and hospitality staff are actively targeted with booking-themed phishing, including messages that impersonate guests and platforms like Booking.com.
- Many of these attacks use ClickFix-style lures, such as fake CAPTCHA or “verification” steps, to trick users into running malicious commands themselves.
- These campaigns work because they exploit real hotel workflows - high-volume, time-sensitive bookings and reliance on third-party platforms, not because staff are careless.
- Initial access can quickly escalate to stolen credentials, malware deployment, guest data exposure, operational disruption, and ransomware.
- Risk is reduced most effectively by focusing on people and process: training staff on booking/OTA impersonation patterns, reinforcing fast reporting, and supporting those behaviors with access and scripting controls.
- Subscribe to All Things Human Risk to get a monthly round up of our latest content
- Request a demo for a customized walkthrough of Hoxhunt






